VPNs have become virtually synonymous with online privacy and security. But while VPNs can offer a significant level of protection, are they truly foolproof? Can someone be tracked even when they are using a VPN?
To put it into perspective, consider the experience of trying to access a website, only to be barred because the website detected your VPN use. Or perhaps you’ve noticed targeted ads popping up, mysteriously reflective of your recent internet activity, despite being connected to a VPN. Both instances raise critical questions: What data are these websites capturing? How are they aware of your VPN usage? And what does this mean for your online privacy?
The goal of this article is to discuss these questions. We aim to reveal the intricate workings of VPNs, their vulnerabilities, and the extent to which they can be tracked. It’s important to understand that the information we provide here is to enhance your awareness and should be used responsibly, adhering to ethical guidelines and legal frameworks.
Tracking Someone Using a VPN: Is It Possible?
To understand if you can track someone using a VPN, you first need to understand exactly how a VPN works. A VPN functions in two key ways to secure your digital footprint and enhance your online privacy:
- Data Encryption: Whenever you use the internet, you’re sending and receiving data. A VPN encrypts this data, creating a secure channel between your device and the VPN server. This encryption renders the data unreadable to any potential eavesdroppers, helping to ensure that your online communications remain confidential.
- IP Address Replacement: Every device connected to the internet has a unique identifier, known as an IP address. This address provides information about your location. When you use a VPN, your original IP address is replaced with that of the VPN server, which could be located anywhere in the world. This can effectively mask your real geographical location and make it appear as if you are browsing from a different place.
These core functionalities of a VPN help create a virtual shield around your online activities, but the level of this shield’s effectiveness can vary, which brings us to the crucial question: Can someone still track you when you’re using a VPN?
As formidable as they may seem, VPNs are not impenetrable. Just like any technology, they have vulnerabilities that can potentially be exploited.
5 Ways to Track VPN Users

Privacy-oriented people use VPNs for various reasons. Some want to access movies on Netflix that are unavailable in their location. Others want to enjoy Bovada crypto casino games or simply establish a secure connection to their office network. Tracking these casual VPN users isn’t exactly a piece of cake.
However, there are some methods which can potentially track or identify someone using a VPN. Please note that some of these methods may infringe upon users’ privacy and may be subject to legal implications.
1. Malware Exploits
When it comes to tracking someone using a VPN, malware can play an insidious role. If your device is infected with malware, it could potentially expose your original IP address and other confidential information to ill-intended actors, even if you’re under the protection of a VPN. But how does this happen?
Some specific types of malware, like the infamous Trojan horse or the Man-In-The-Middle (MITM) attacks, are designed to bypass the encryption of a VPN. A Trojan horse can pretend to be a harmless program, tricking the user into downloading it.
Once on your device, it can access your system and send sensitive data to the hacker. On the other hand, MITM attacks work by intercepting and altering the communication between your device and the VPN server, which could potentially reveal your actual IP address.
VPN Doesn’t Protect You From Malware
VPNs are great at maintaining your online privacy and security by encrypting your connection and changing your IP address. However, they aren’t built to protect your device from malware infections. If you click on a malicious link or download an infected file, a VPN can’t prevent the malware from infiltrating your device. Once inside, the malware can potentially relay your confidential data back to the hacker, regardless of whether you’re connected to a VPN.
How Hackers Use Malware to Target VPN Users?
Hackers employ various techniques aimed at infiltrating a user’s device with malware, and VPN users are no exception. Here’s a breakdown of some common methods they use:
- Phishing Emails: Phishing is a popular technique among cybercriminals, designed to exploit the user’s trust and lack of attention to detail. In a typical phishing attempt, the hacker sends an email that appears to be from a trusted source (a bank, a popular online platform, or a work colleague, for example). This email contains malicious links or attachments. When the recipient clicks on the link or opens the attachment, malware is installed on their device. Even though a VPN can hide your online activities, it won’t protect you if you fall for such a scam.
- Infected Websites: Sometimes, hackers set up websites filled with enticing content to lure unsuspecting users. These sites are often booby-trapped with various forms of malware. As soon as you click on a seemingly harmless link or download a file, you could unintentionally install malware on your device. Again, a VPN would not protect you from this kind of attack.
- Social Engineering: This technique involves manipulating the user into divulging confidential information, like passwords or credit card numbers. In the context of VPN usage, a hacker may impersonate a VPN provider and trick the user into providing their login credentials. Once the hacker has these, they can potentially bypass the VPN and gain access to the user’s online activities.
- Software Vulnerabilities: Hackers are always on the lookout for software vulnerabilities they can exploit to introduce malware. Outdated software, including older VPN versions, are particularly susceptible to these attacks. Therefore, keeping your software and apps up-to-date is essential for maintaining your device’s security.
These techniques highlight the importance of practicing good cybersecurity hygiene. While a VPN can protect your data in transit and hide your location, it won’t prevent malware infections if you fall into these traps. Always stay vigilant, use strong and unique passwords, don’t click on suspicious links, and keep your software up-to-date to mitigate the risk of malware attacks.
2. Browser Fingerprinting: Unmasking VPN Users
Browser fingerprinting is an advanced tracking technique that collects data about your device and software to create a “fingerprint” that is uniquely yours. Although a VPN can hide your IP address, it cannot alter the unique combination of software and hardware details that constitute your browser fingerprint.
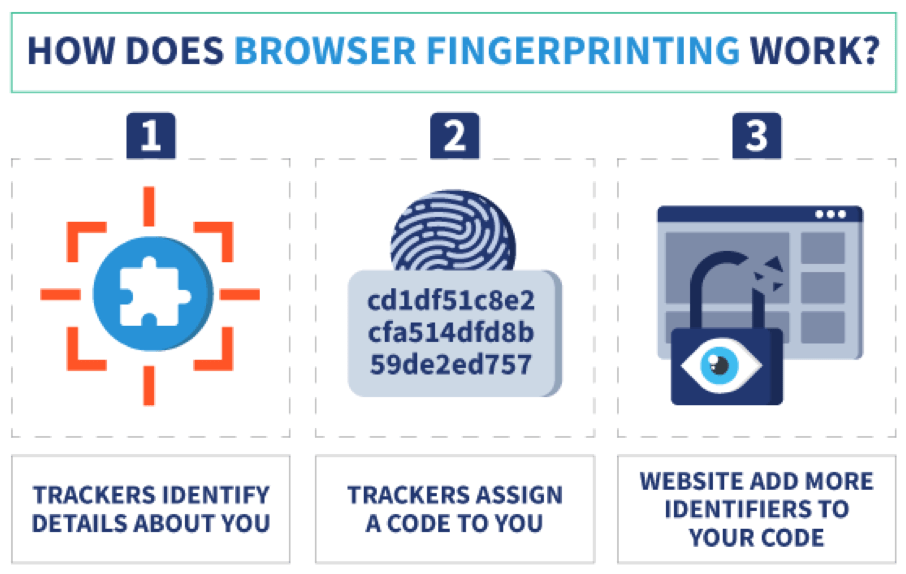
So, how does this technique allow someone to track a VPN user? Here’s how:
1. Data Collection
When you visit a website, the site collects information about your device and your browser settings. This can include your operating system, installed software, time zone, screen resolution, hardware specifications, and much more.
All these details may seem insignificant in isolation, but combined, they can form a unique profile that can be used to identify you.
2. HTML5 Canvas Fingerprinting
One of the more advanced forms of browser fingerprinting involves the use of the HTML5 Canvas element. This feature allows websites to create images in a browser, which can then be used to gather even more information about your device.
When a website uses the HTML5 Canvas to draw an image, slight differences in how your device renders the image can be detected. These differences can be due to the type of graphics card used, the installed fonts, the browser version, and other such factors. Even though you might be using a VPN, this rendering process remains unique to your device and helps create a more detailed browser fingerprint.
Tracking VPN Users
A website designed to track VPN users could take advantage of these fingerprinting techniques to recognize return visits from the same device, even when the IP address changes due to the VPN.
For example, let’s say you visit a site that uses browser fingerprinting. The first time you visit, the site collects your fingerprint data and logs your VPN IP address. The next time you visit, even if you connect from a different VPN server, the site can still recognize your browser fingerprint and connect it to your past activity.
Please note that while these techniques can identify a device, they cannot directly link that device to a specific person. Also, some countermeasures like using browser plugins or changing browser settings can help minimize the data collected for fingerprinting.
3. Exploiting Vulnerabilities in VPN Protocols
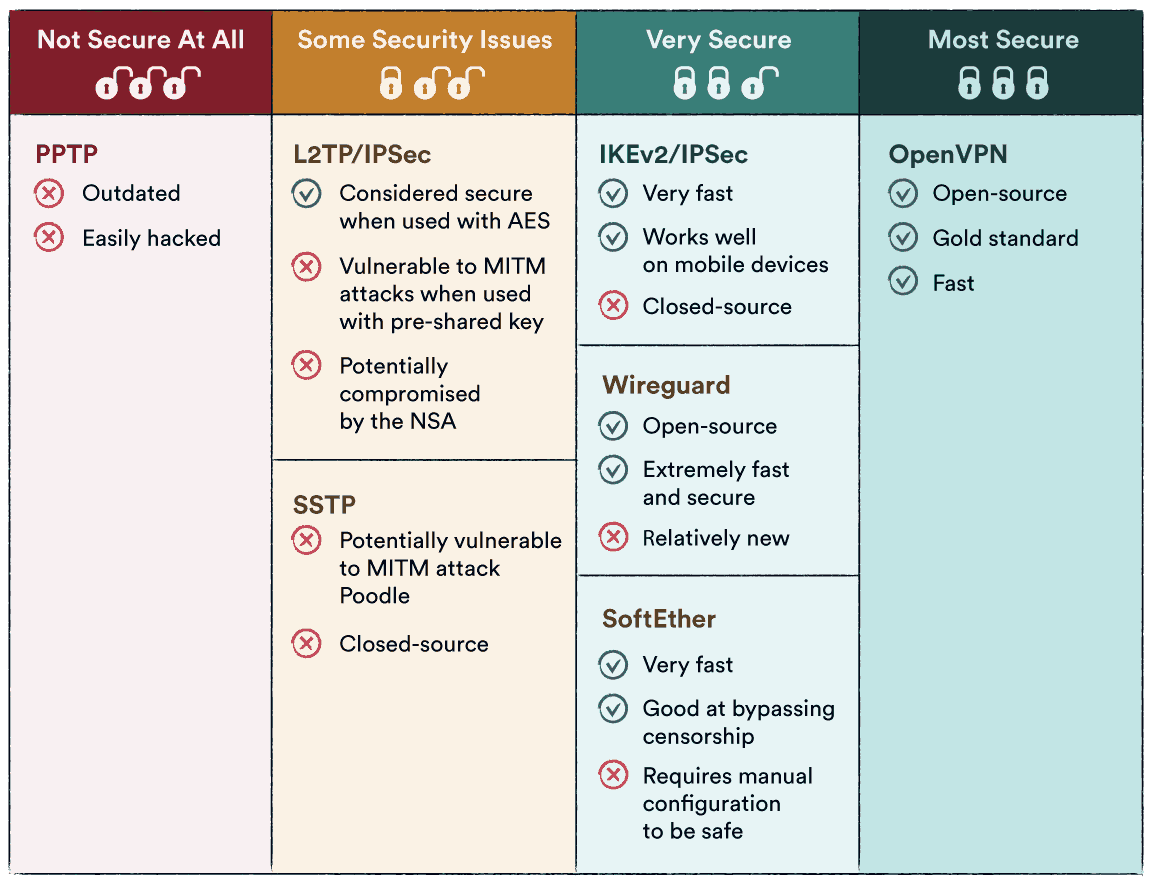
VPN protocols are the rulesets that define how data is transmitted between your device and the VPN server. Different VPN services use different protocols, with OpenVPN, WireGuard, and IPsec being some of the most common in consumer VPNs.
However, these protocols aren’t infallible. If a vulnerability exists within the protocol you’re using, this can be exploited by hackers, potentially leading to your VPN connection being compromised and tracked. Let’s delve deeper into this:
What Makes VPN Protocols Vulnerable?
Every VPN protocol has its strengths and weaknesses. Some provide blazing speed but may fall short when it comes to securing data. Others might offer robust security but compromise on connection speed. Then there are the matters of design flaws and improper configuration.
A newly developed protocol might have undiscovered flaws that hackers can exploit, while a poorly configured VPN client can present opportunities for attackers.
A Case Study: The PPTP Protocol
The PPTP (Point-to-Point Tunneling Protocol) serves as a prime example of protocol vulnerabilities. Once widely used, PPTP is now considered insecure due to reports of successful cracking attempts, notably by the NSA.
Despite these security concerns, some VPN services still offer PPTP as a protocol option, leaving users potentially exposed.
The Implication of Protocol Vulnerabilities
Let’s say you’re using a VPN protocol with a known vulnerability, such as PPTP, to browser your favorite website. A skilful hacker who knows about this vulnerability could exploit it to infiltrate your VPN connection. They might be able to unmask your real IP address, track your activities, or even intercept your data.
What Can You Do About It?
To mitigate the risk posed by protocol vulnerabilities, always make sure to use a VPN that offers the latest and most secure protocols. OpenVPN and WireGuard are currently known for their robust security. Additionally, regularly updating your VPN client ensures that you benefit from ongoing improvements and patches that secure any newly discovered vulnerabilities.
It’s also crucial to be aware of the VPN protocol you’re using. If your VPN service doesn’t allow you to choose or doesn’t clearly state which protocol it’s using, it might be time to consider switching to a more transparent service.
4. Cryptographic Attacks
To maintain your privacy while using a VPN, your web traffic is transformed into an obfuscated code using an encryption cipher. This cipher, essentially an algorithm, handles the encryption and decryption of your data. To further fortify your connection, a hash authentication is applied. Unfortunately, these cryptographic systems aren’t invincible and can become the targets of attacks aimed at tracking VPN users.
Let’s break this down:
Common ciphers in VPN services include AES, ChaCha20, and the less common Blowfish. These ciphers work hand in hand with a key length, indicating the number of digits in the encryption key.
Longer keys generally equate to more security, making AES-256 more secure than AES-128. Meanwhile, hash functions like SHA-1 add an extra layer of security.
As technology advances, so does the ability to break older ciphers and hash functions in a shorter timeframe. For instance, the once widely-used SHA-1 hash function is now cryptographically broken, and the Blowfish cipher is susceptible to ‘birthday attacks’. If your VPN connection uses these outdated cryptographic systems, it’s potentially hackable.
What is the Ideal Cipher to Use?
A VPN should ideally use nothing less than the AES-128 cipher for data encryption. However, AES-256 offers even more security.
Ways to Protect Yourself
To shield yourself from potential cryptographic attacks, ensure your VPN employs a robust and up-to-date encryption cipher, such as AES-256 or ChaCha20. Regularly updating your VPN service also helps to keep these cryptographic functions updated and more resistant to attacks.
As a golden rule, always opt for a VPN that uses a robust, modern encryption cipher and keep your VPN client up to date.
5. Monitoring Data Leaks
Using a VPN creates a secure passage for your data to traverse through the internet, much like a tunnel. But, as with any tunnel, there are chances for leaks. This doesn’t necessarily mean your VPN connection is broken; however, it might still expose your identity or online activities. This phenomenon is commonly known as a ‘VPN leak’.
For instance, your actual IP address might get revealed if your VPN fails to encrypt all internet requests, including IPv6 ones, made by your browser. The same could happen if the VPN doesn’t reroute WebRTC connections correctly.
Another form of leakage occurs when your Domain Name System (DNS) requests are being processed by your Internet Service Provider (ISP) instead of the VPN service. This mishandling of requests can expose your browsing history and other online activities, which is termed a ‘DNS Leak’.
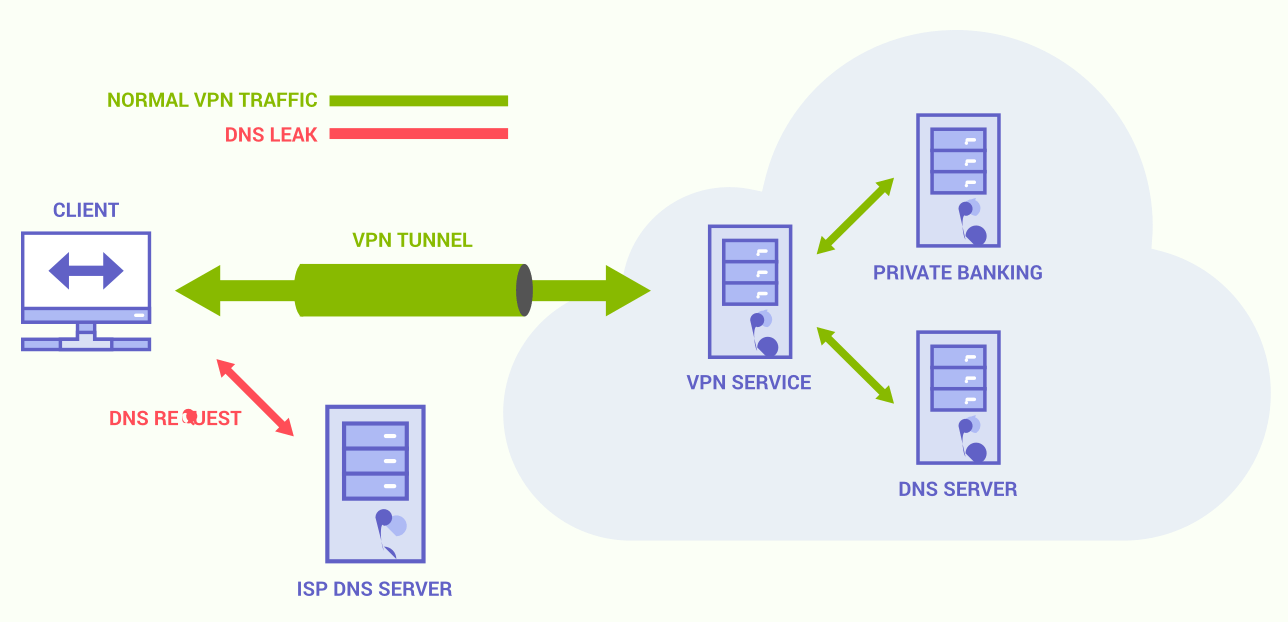
Also, if your VPN’s kill switch, a security feature designed to stop all internet traffic if your VPN connection drops, malfunctions, it could lead to further exposure.
To conclude, while a VPN can significantly increase your online privacy and security, it is not a one-stop solution. Various methods and techniques, ranging from malware attacks to exploiting vulnerabilities in VPN protocols, browser fingerprinting, cryptographic attacks, and VPN leaks, can potentially expose a user’s data like IP address. Some of these methods require advanced technical skills, and many pose legal and ethical implications.
Remember, it’s crucial to pair your VPN use with other cybersecurity best practices. This includes regularly updating your VPN software, using strong, unique passwords, and being mindful of phishing attacks and suspicious websites.
Moreover, choosing a reputable VPN provider with a robust security infrastructure is vital. Look for providers who offer the latest encryption standards, possess no-leak technology, and have a solid privacy policy.
FAQs
Can police track VPN?
No. The police aren’t able to track live VPN activity. However, with a court order, they can ask your Internet Service Provider (ISP) for logs of your connection or usage. Since your ISP is aware you’re using a VPN, they can point the police to your VPN provider. Now, whether your VPN provider shares this information or not depends on things like the laws of the land and the privacy policy of the VPN service.
Can my employer track my location through VPN?
Yes. Your employer can track your location using the IP address assigned by your ISP. However, the accuracy of the location can vary depending on the ISP
Can Governments track VPN?
Yes, governments can potentially track VPN usage. While VPNs encrypt your data to keep it private, they still need to interact with your Internet Service Provider (ISP). Your ISP can see that you’re connected to a VPN, even if it can’t see what you’re doing. If a government agency orders an ISP to release information about its customers, the ISP must comply.
From there, the agency can request information from the VPN service. Whether the VPN service complies depends on their jurisdiction and privacy policy. Some VPN services are located in countries with strict privacy laws and do not keep user activity logs, making it more difficult for governments to track users.
However, it’s important to note that the level of privacy and anonymity a VPN provides is not absolute. In exceptional cases, advanced techniques and resources may be used by government agencies to track VPN users.
Can company VPN track your activity?
Yes, if you’re using a company-provided VPN, they have the potential to track your online activities. When you use a VPN, all your internet traffic is routed through the VPN server. If the VPN server is owned and managed by your company, they have the ability to log this traffic.
This means they could see the sites you’re visiting, when you’re visiting them, and potentially even the information you’re sending and receiving, though the latter is less common. However, it’s important to note that whether a company decides to track your activities or not depends on their individual policies.
Some companies may choose to respect their employees’ privacy and not monitor their activities, while others might have policies in place that allow for this kind of surveillance. Therefore, it’s always a good idea to read and understand your company’s IT policy.
Can ISP track VPN?
Yes, your Internet Service Provider (ISP) can technically see that you’re using a VPN, but what they cannot see is what you’re doing while connected to the VPN. When you use a VPN, all of your traffic is encrypted and routed through the VPN’s server.
This means that while your ISP can see that data is being sent and received, they can’t actually read the contents of that data or see which websites you’re visiting. That information is hidden by the encryption provided by the VPN. However, your ISP can see the amount of data being used and the times you’re connected to the VPN.
It’s important to remember though, not all VPNs are created equal. Some may leak information or have weaker encryption, so it’s important to choose a reputable VPN provider.
Can company track your computer without VPN?
Yes, a company can track your computer without a VPN, particularly if it’s a work-issued computer. Many businesses install monitoring software on their computers to track productivity, ensure compliance with company policies, and protect against potential legal liabilities.
This software can monitor which websites you visit, how much time you spend on certain tasks, and even what you type. It can also capture screenshots of your activities. If you’re using a personal computer for work purposes, your company might have less visibility, but they can still potentially see information sent over their networks or stored on their servers.
If I use a VPN can my ISP track what I download?
No. When you use a VPN, your ISP can’t directly see what you download or where your internet traffic is going. That’s because a VPN encrypts your data and hides your online activities by sending your traffic through a server located elsewhere.
However, your ISP can still see that you’re using a VPN and the amount of data being transferred. If your VPN connection drops unexpectedly, or if there are leaks (such as DNS leaks), your ISP might be able to see some of your internet activity.
Can VPN track your location?
A VPN is designed to mask your actual location by routing your internet traffic through a server located elsewhere. When you’re connected to a VPN server, the server’s location is what appears to outside observers, not your actual geographic location.
However, it’s important to note that your VPN provider could theoretically see your real IP address and therefore your location. So yes, VPN can track your location.
If we use VPN can anyone track me?
Using a VPN doesn’t make you completely untraceable. When connected to a VPN, your internet traffic is encrypted and routed through a server in a location of your choice. This makes it difficult for anyone, including your ISP, to see what you’re doing online or where you’re physically located.
So, while a VPN provides a higher level of privacy and security than not using one, it’s not a guarantee of absolute anonymity. You someone can still trace you using the menthods discussed in this article.
Related Posts:
- VPN Scam – How to Spot Scam VPN Apps?
- CroxyProxy VPN – Unblock YouTube, Instagram and Facebook
- How to Stay Anonymous on the Internet – VPN is not the only Solution
- Top 5 VPN Services: An In-Depth Guide to Their Distinct Advantages
- Why You Need a VPN for Your Android Device
- Using a VPN with uTorrent makes torrenting a much safer experience
- Creating your own VPN server on DigitalOcean & Amazon EC2 for free
