Since the number of cyberattacks has increased, cybersecurity has become a significant issue for both organizations and individuals. The Internet has made it easier than ever to save and share data, but it has also created the potential for cybercrime. As cybersecurity precautions have become more prevalent, cybercriminals have shifted their tactics as well.
According to the McKinsey report, cybercrime will cost companies $10.5 trillion by 2025. As a result, cybersecurity experts should always keep a close eye on critical developments. Hence, cybersecurity is a never-ending war between the protectors of information and those who seek to steal it.
In this article, we will discuss eight cybersecurity trends that are likely to be of significance in 2024 and potential opportunities for them.
8 Cybersecurity Trends and Technologies in 2024
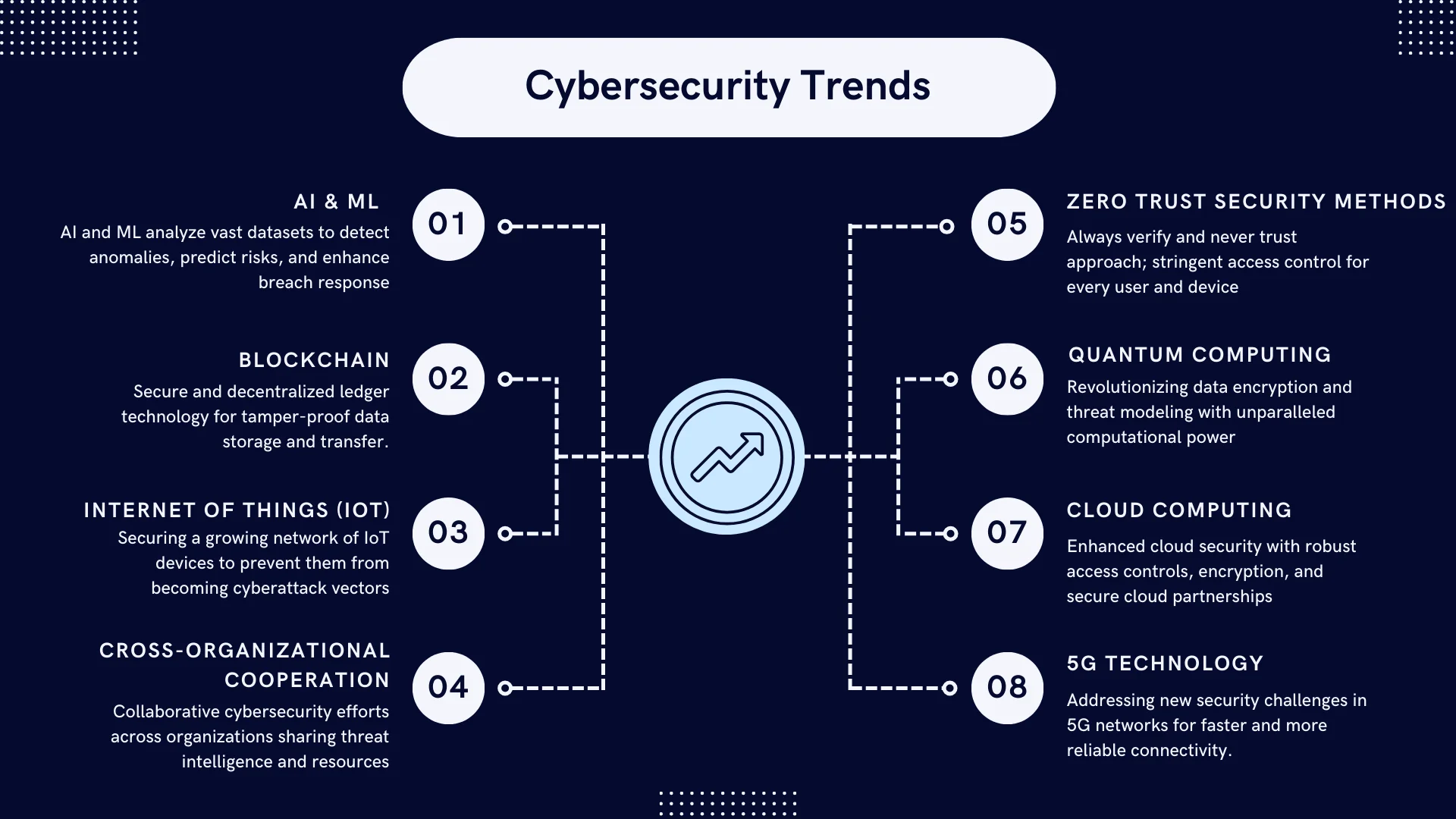
1. Artificial Intelligence and Machine Learning
One of the most significant developments in cybersecurity is the use of artificial intelligence (AI) and machine learning (ML). AI and ML can scan huge data sets and detect patterns and anomalies that may indicate danger. By identifying and preventing cyberattacks in time, enterprises can reduce the level of harm inflicted on them as well as lower the impact of breaches.
Also, AI-driven cybersecurity tools can take over repetitive security roles and let people proceed to more complex tasks. Through past statistics and patterns, AI and machine learning can also predict future cyber risks. Therefore, the companies can prevent threats in advance, which decreases the effectiveness of possible attacks.
2. Blockchain Technology
Blockchain technology is another rising trend in cybersecurity. A blockchain is a distributed ledger that ensures the safe storage and transfer of information. As a distributed network, blockchain is incomparably more difficult to break into, which makes it much preferable for high-security-based applications.
Due to the high risk of data breaches in industries such as banking, healthcare, and the government, blockchain is currently being implemented at many different organizations for cybersecurity purposes.
3. Internet of Things (IoT)
As the popularity of IoT increases, cybersecurity is also likely to be affected considerably. It has become common to use IoT devices for tracking important infrastructure and systems. However, IoT devices do not have enough security measures to prevent cyber thieves from using them.
Thus, companies must enhance their security practices to protect against potential IoT-based cyber threats. Some IoT devices may need firmware and software updates, or in some cases, they might have to be replaced by more secure ones that offer two-factor authentication.
See also: Improve Your IoT Gateway Security: from Hardware to Software
4. Cross-organizational Cooperation
Another important development in cybersecurity is a greater focus on cross-organizational collaboration. In the past, firms have been shy about sharing details about cyber threats for fear of exposing their weaknesses. However, in the past few years, this has been changing as corporations understand that cyber risks may be too complex for a single firm to handle.
Therefore, most companies are banding together and sharing knowledge to secure themselves from any cyberattacks. The sharing includes threat information, best practices, and resources, as well as operations in joint cybersecurity activities.
5. Zero Trust Security Methods
National security is dependent on cybersecurity, and governments try to provide the necessary protection of valuable infrastructure from cyberattacks. For instance, the increasing use of ‘zero trust’ security practices, where access to sensitive information is managed and controlled at all times.
By using this approach, malicious access is restricted, and cyber-attacks are prevented. In addition, governments are allocating resources to R&D so that they can maintain their lead over the latest cyber threats and come up with newer technologies for defensive needs.
This can be done through the development of new encryption methods or by applying quantum computing to crack complex codes.
6. Quantum Computing
In the future, cybersecurity will be thoroughly influenced by quantum computing because it will completely alter data protection and processing as we know it today. Cybersecurity methods use encryption mainly because some mathematical problems are difficult for conventional computers to solve.
The current encryption technologies could only be updated if quantum computers could solve such problems much more quickly. This means that quantum computers can be applied to crack the current encryption, potentially compromising cybersecurity. In contrast, quantum computers could generate unprecedented encryption methods that would offer high levels of data security.
A quantum algorithm of detection and response to cyber attacks as the potential application for quantum computing in cyber security is proposed. These algorithms are capable of analyzing large amounts of data to identify patterns that indicate a potential threat, enabling businesses to detect and respond faster during cyberattacks. In addition, quantum algorithms can be used to predict future cyber threats by looking at past data and trends.
7. Cloud Computing
With cloud computing on the rise, data security will become a major challenge because sensitive data is being accessed without authorization. Data is accessible by cyber thieves having gained access to the provider’s cloud or stolen login credentials. This risk can be addressed through the use of robust access controls and encryption, coupled with partnering with reliable cloud providers that have solid security measures in place.
Other security challenges raised by cloud computing include data breaches. This can occur when cyber thieves attack the servers of a cloud provider and obtain vital information that is stored on them. This can be achieved by validating that data is encrypted in transit and at rest, as well as ensuring cloud providers employ strong security measures.
It is projected that large corporations will leverage the quantum internet to safeguard data, while ordinary consumers may continue to use the conventional web. In order to address these security concerns and regulatory demands, several cloud providers integrate numerous safety features such as encryption, access limitation, and monitoring.
Organizations might also opt for multi-factor authentication, intrusion detection systems, and firewalls to enhance the security of their cloud-stored data.
8. 5G technology
5G integration into telecommunications presents opportunities as well as threats to cybersecurity. With 5G technology, businesses and applications can communicate faster and more reliably than before. However, 5G opens up new security vulnerabilities because malicious actors are able to exploit more data.
5G networks are designed to support the billions of devices, making them an enticing target for cybercriminals. Additionally, 5G networks use software-defined networking or SDN, making them more exposed to software vulnerabilities. The best way to mitigate this threat is to implement secure measures, such as encryption, access control, IDSs, etc., and work with 5G network providers that have strict security policies.
A second concern related to 5G technology is the possibility of IoT devices being hacked. IoT devices are to be an integral part of the 5G ecosystem, but they have limited computational power and security characteristics that make them vulnerable. As a precaution, enterprises need to ensure that sensitive information is encrypted in transit and at rest; they also must select trustworthy 5G providers with strong privacy controls.
Final Words
With the dawn of a new year in 2024, cybersecurity moves forward with revolutionary changes and joint efforts that carry great innovations. Also, an alliance between AI and Machine Learning, blockchain technology adoption, increased IoT security, and cross-organizational cooperation are not only trends but vital movements shaping the future of digital safety.
Furthermore, the introduction of Zero Trust Security methods, alongside anticipation of cybersecurity’s impact on quantum computing, and efforts to protect Cloud Computing infrastructures and 5G networks, represents a proactive effort toward creating a more robust and resilient cyber environment.
Cybersecurity is driven by technology, and strategic partnerships weave this fabric. These trends will not only help us to resist contemporary threats but also build a future digital environment that is secure.
Related Articles:
- How Cybercriminals Are Leveraging AI Tools for Cyberattacks
- 5 Reasons Why Cybersecurity is Important Now More Than Ever
- 5 Cybersecurity Tips to Protect Your Small Business from Cyber Attacks
- The Role of Artificial Intelligence in CyberSecurity
- How Do Computer Scientists Ensure Cybersecurity
- 8 Ways to Boost Your Team’s Cybersecurity Awareness
- Why Interoperability Presents a Weakness in Cloud Computing
- 9 Tips for Protecting Your Company and Consumer Data
- Understanding and Protecting Your Data Online
