The large network of interconnected physical items that share data with other devices and systems online is known as the internet of things (IoT).
It gives meaning to the idea of ubiquitous connectivity for corporations, governments, and consumers with its built-in administration, monitoring, and analytics, but the hazards are easily disregarded.
Every internet-connected device has potential security risks. IoT security breaches can leave people with psychological scars and cost businesses money.
Where Might an Internet of Things System be Vulnerable?
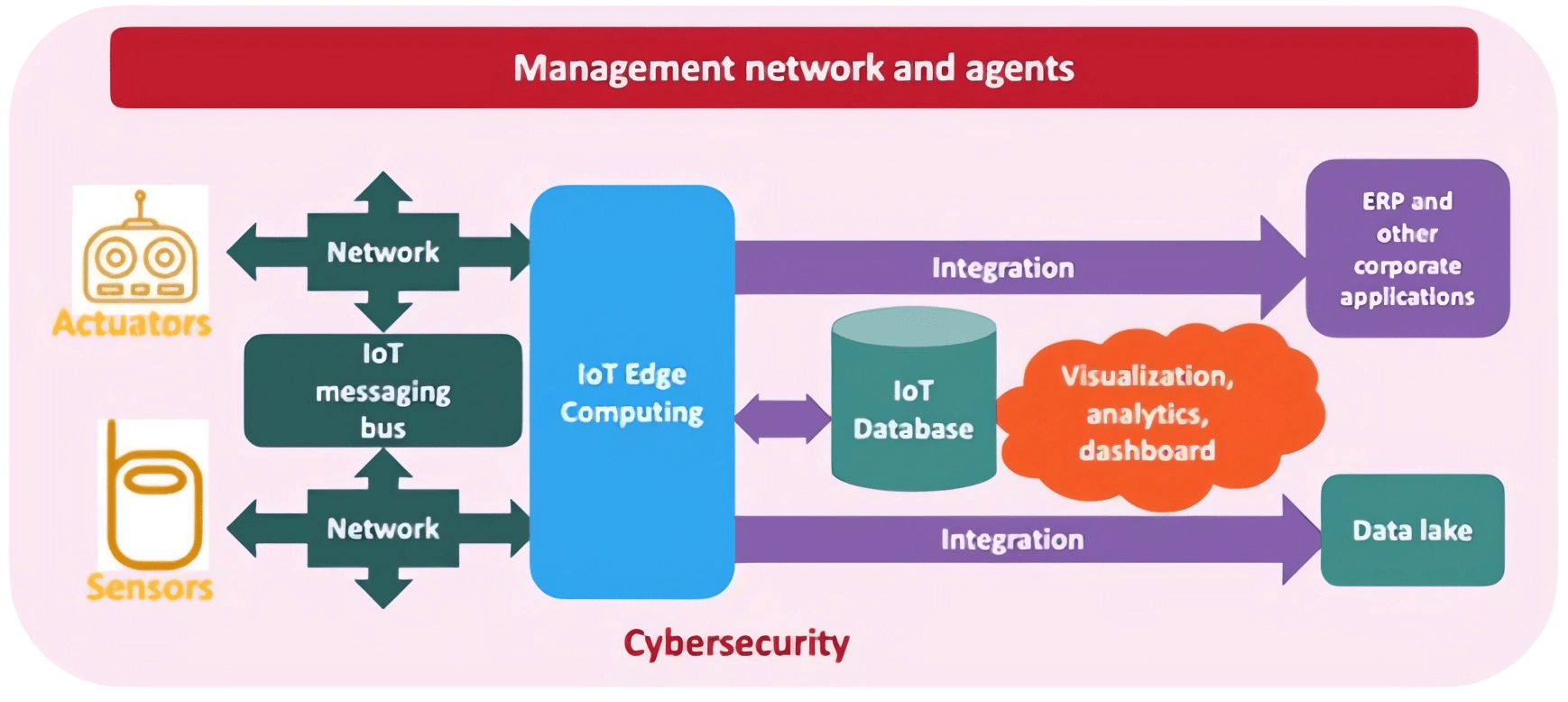
An IoT system infrastructure can be divided into three parts, and a network breach could happen if one of these parts has a weakness:
The edge client: sensors, actuators, cameras in home, office buildings, and manufacturing field
the IoT gateway: that gathers data from end points and prepares for sending to the cloud platform before doing so
The cloud platform: provides the standards and services required for integrating, controlling, and protecting various IoT applications and devices.
Users: blunder, carelessness, or ignorance when using the IoT system.
Security of IoT Gateways is Crucial for the Entire IoT Systems
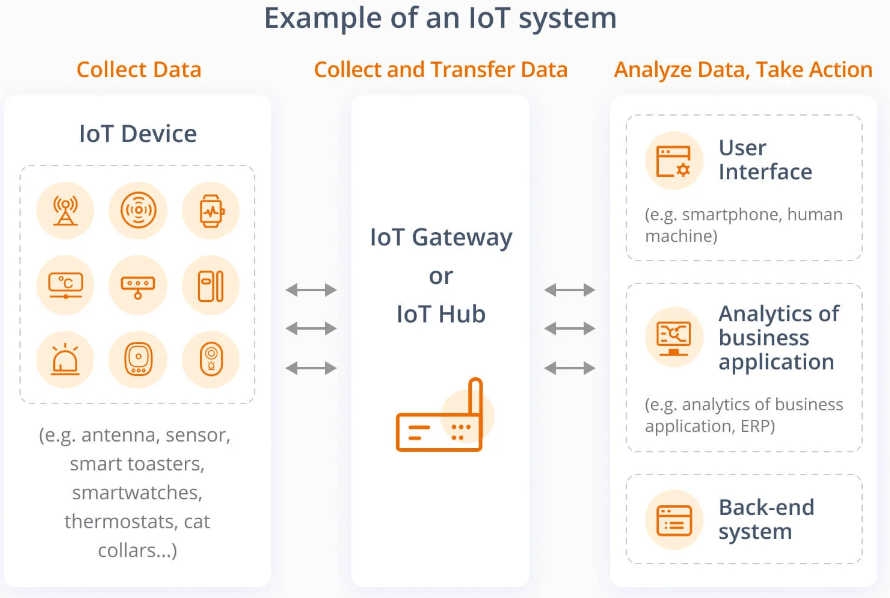
An IoT gateway serves as the brain of the IoT system for the majority of commercial and industrial users. It assumes responsibility for handling data, processing it, and sending it to the cloud.
The order of the data transfer is like this: edge device > IoT gateway > cloud.
IoT gateways are therefore charged with the transmission and processing of data and furnished with a variety of hardware and software that is capable of doing the job.
On the other side, this adds a potential attack vector to the IoT system.
How to Ensure the Security of IoT Gateways

Using Chips with Physical Counter Measures
It is crucial to protect data stored in the gateway chips. A typical industrial RS485/232 gateway will probably have a gigahertz of processing speed and a gigabyte of RAM.
To improve IoT gateway chip security, choosing chips already having security features for data storage, including key storage, is a common method.
Secondly, we shouldn’t allow unauthorized access to data stored in flash or EEROM. Finally, it’s important to protect the data that is stored in RAM while a system is running.
Uplift the Access Threshold of Data Communication
Wireless data transfer is like yelling in the street. Everyone who understands your language will be able to get the information. For most resource-constrained IoT applications, information is typically transferred as plain text.
If there is no encryption, data interchange is no longer confidential because it is quite simple for an unauthorized or undesirable person to eavesdrop on this crucial information.
Leverage Encrypted Algorithms to Ensure Data Confidentiality
Using cryptographic techniques, both transmitted and stored data should be protected. With the aid of a secret key and encryption techniques, the transmitter transforms the private data into what appear to be random bytes before transmitting it over the internet.
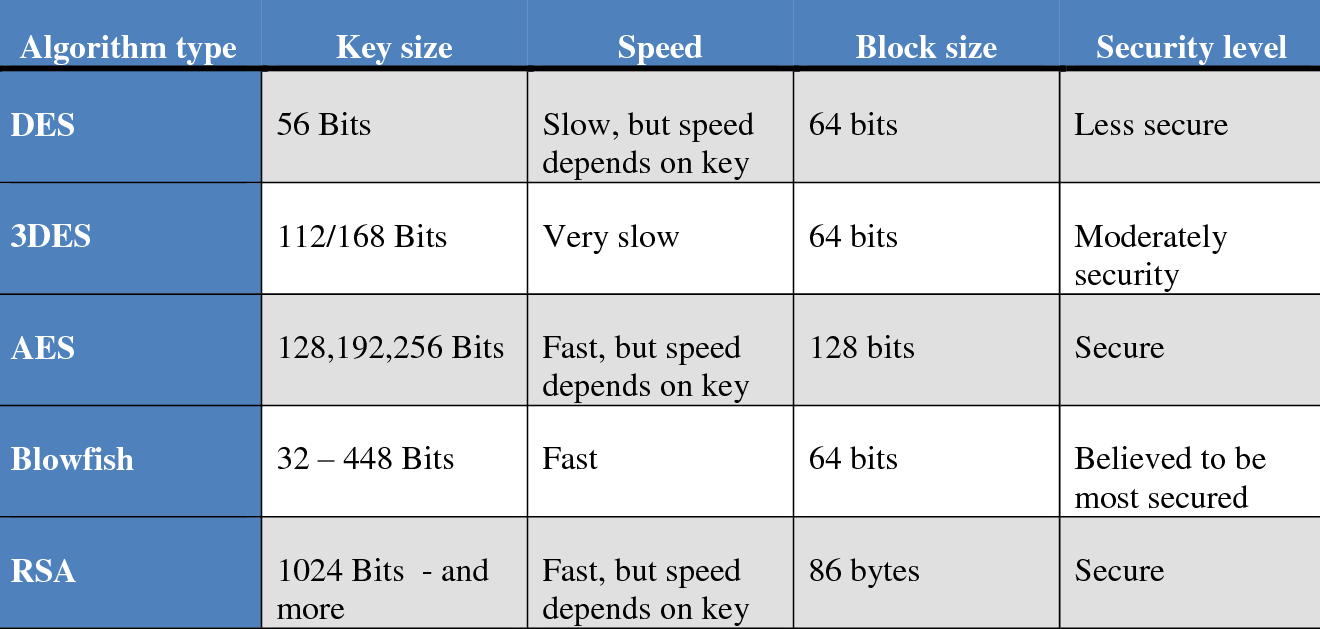
The secret key, which is the only way to decrypt these random bytes or encrypted data, is only known by the recipient. DES, RSA, and AES are commonly used encryption techniques.
For WIFI, you can use WPA2 authentication, and for BLE, Z-Wave, and ZigBee, you can use AES-CCM.
Utilize Hash Function to Ensure Data Integrity
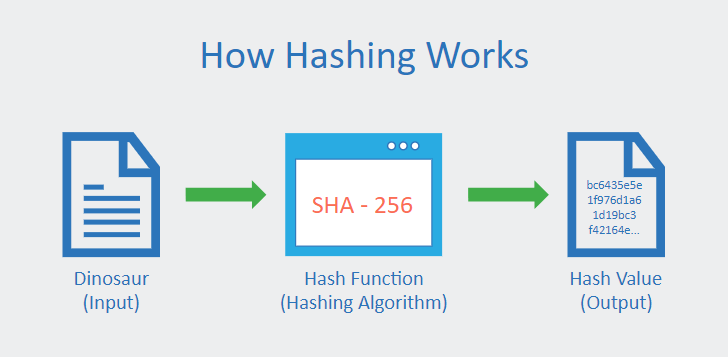
The most popular way to ensuring data integrity is hashing. This is accomplished by the transmitter transforming random bytes of fixed length from variable-length data. These random bytes are delivered across the internet along with the actual data.
The receiver then applies the same technique employed at the source to transform the variable-length data received into random bytes. The receiver’s estimated random bytes match the ones that were sent.
The receiver will then be able to verify that the data is accurate. If they don’t, then either the data or the random bytes have been altered, and the receiver is aware that the information cannot be trusted. A few popular cryptographic hashing algorithms are MD5, SHA-1, SHA-256, etc.
Check TLS or SSL Certificate before Data Exchanging
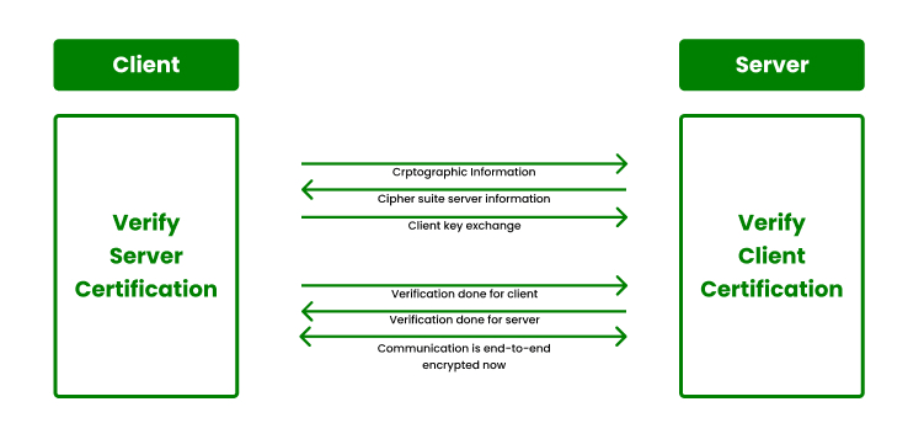
While data is transferred between the server and the client, the IoT must confirm the server’s legitimacy before transmitting sensitive data and in order to guarantee data confidentiality. Requesting and checking the server’s TLS or SSL certificate is a standard way to authenticate a server.
TCP/IP’s transport layer and application layer are separated by a security protocol known as transport layer security, or TLS. To establish a secure connection between an IoT device and a cloud server that permits the transmission of data securely, TLS or SSL uses a combination of the aforementioned industry standards.
Using More Secure ECC for Web Traffic Encryption
Elliptic Curve Cryptography (ECC) is a key-based method of data encryption that is frequently employed in cryptocurrency implementations for digital signatures.
It is a substitute for RSA that has gained popularity recently because of its smaller key size, higher level of security, and quicker encryption and decryption times.
Due to these benefits, IoT gateway web applications also use ECC. Here is an example of using ECC encryption in IoT gateway.
Keep Software and Firmware Updating Regularly
Keeping your IoT gateway hardware and software up-to-date is one of the best ways to keep them safe. Manufacturers of IoT gateways occasionally discover flaws in the firmware of the hardware and offer firmware updates.
When you see the notification on the front end, updating these frequently is as easy as clicking a button. This is similar to software as well. Make sure to keep your gateway’s operating system updated, if it has one.
Takeaway
In order to protect data privacy and secure the security of your home or business, it is crucial to address security threats. In this article, we discussed how to strengthen the security of your IoT gateways.
The process of IoT security is continuous. To ensure an updated security plan, you must configure it to be as robust as feasible by default and then periodically check it. It is advised that you create a robust IoT security system.
Every IoT system must start with a consideration of the threat vectors that you may encounter, depending on your physical situation and human considerations.
For instance, are the latest IoT gadgets dangerous? Do those credentials still need to be provided to those with higher access? And plan a periodic meeting to discuss how these situations have altered as well.
Related Posts:
- Cost-effective IoT Components For Your Next IoT Project
- How to Detect Data Loss in Your Organization?
- Security Risks of Using a Multiple USB-C Hub: How to Protect Your Data
- Why Partitioning Your Hard Drive Is a Smart Move for Your Data
- Importance of Securing Your Cloud-Native Applications
- Three Types Of Cloud Storage And Their Benefits
- How to Conduct a Cloud Security Assessment
