Have you ever found yourself pondering over how hackers manage to crack email passwords? Or maybe you’ve been curious about the process involved in hacking into someone’s email account. It’s a topic that often sparks a mix of intrigue and concern.
At first glance, hacking into an email account seems like an impossible task. We’re often told that by using strong passwords, enabling two-factor authentication, and adhering to basic security checklists, our email accounts become virtually impenetrable. This leads many to believe that email hacking is an extremely difficult, if not impossible, task for someone without advanced computer security knowledge.
However, the truth is a bit more complex. While it’s certainly not easy or straightforward, a well-planned attack can sometimes catch even the most security-savvy user off guard.
Email hacking doesn’t just rely on technical know-how; it also requires a blend of creativity and patience. And it’s important to note that often, the weakest link in email security isn’t the technology itself, but the people using it.
I receive dozens of emails daily from individuals requesting help to hack into their partner’s email, suspecting infidelity, or from victims whose email accounts have been compromised by someone they know.
It’s crucial to understand that most email hacks are a result of user negligence rather than any shortcomings of the email service provider. This is a hard truth, but acknowledging it is vital. Hackers typically exploit human vulnerabilities rather than technical loopholes.
Humans are the weak link in all security systems and hackers exploit the same weakness.
In this post, I aim to shed light on this topic by detailing four fundamental methods commonly used in email hacking. These aren’t just tricks of the trade for hackers; understanding them can also help you safeguard your own email account.
So, let’s dive into the effective techniques used by professional email hackers, and perhaps more importantly, learn how to protect ourselves against such attacks.
See also : Modern ways to Hack Email
4 Practical Ways to Hack Email Account in 2024

Although there are several sophisticated methods for hacking email accounts, especially for those targeting high-profile or high-value users, these methods generally revolve around four fundamental techniques. Despite the evolution of hacking strategies, these core methods remain the backbone of most email hacking attempts.
1. Using Spy App: Hack into Someone’s Email without their Password
Ever wondered how hackers can sneak into someone’s email without ever knowing their password? It often starts with something called a spy app. This nifty bit of technology is essentially a small piece of code that, once installed on the target’s device, becomes a digital detective.
It keeps track of everything typed on the keyboard, from emails to social media activity, and even browsing history.
This method is surprisingly straightforward and alarmingly effective. Hackers use it to swipe all sorts of sensitive details, like email passwords and credit card information. The catch? You either need direct physical access to the target’s device or, if that’s not possible, get a bit creative and find a way to encourage the target to install the app themselves.
Spying on Smartphones
Breaking into someone’s email account doesn’t always require knowing or resetting their passwords. With a spy app like mSpy, recommended by our team at Hacker9, you can hack into the user’s email account—reading sent and received emails, checking out contacts, and much more—all without ever needing to reset their password.
The Spy app isn’t just about email hacking. It’s a versatile tool that logs phone calls, spies on text messages, monitors WhatsApp, and even records passwords. Its appeal lies in its compatibility with both Android and iPhone devices. With the Spy app, email hacking becomes less about cracking codes and more about smart, discreet monitoring.
Here’s how a spy app (mSpy) works:
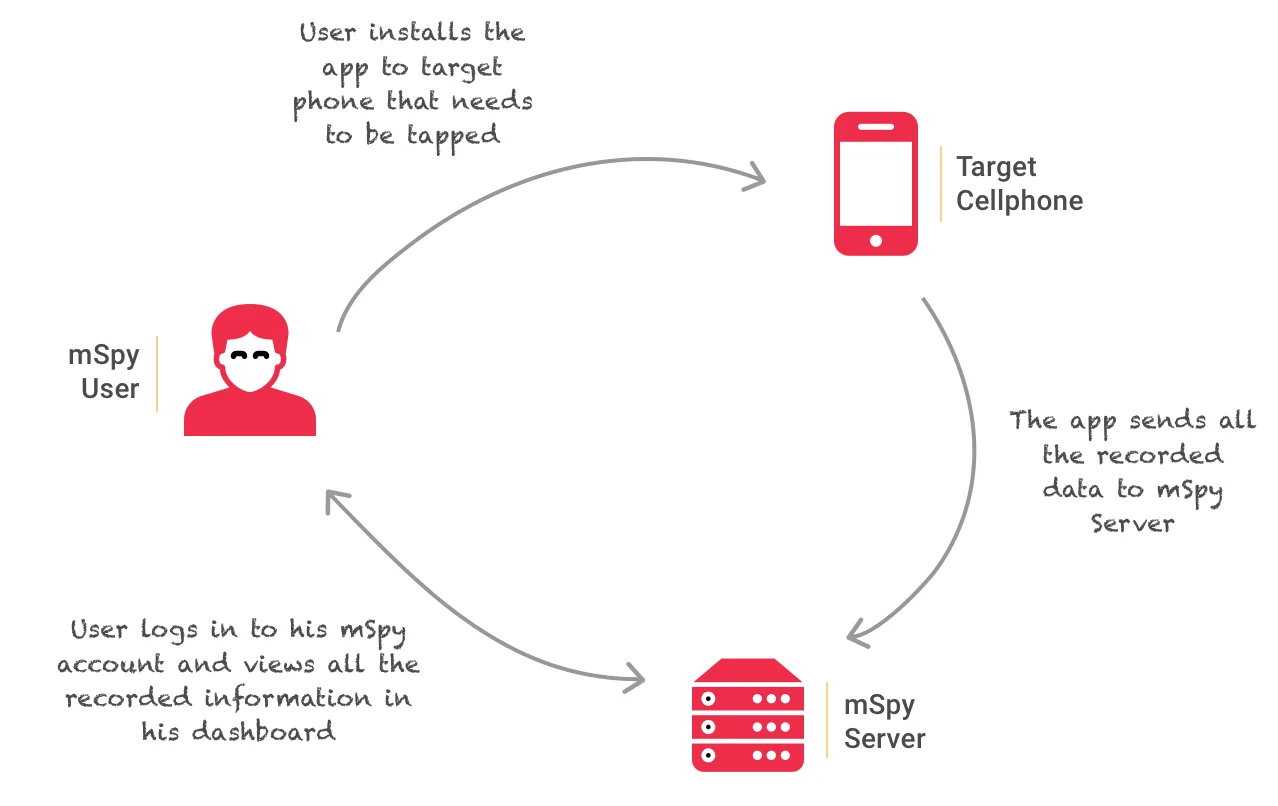
Detailed guide: how to tap a cell phone.
The trickiest part of using a spy app like mSpy is the initial installation on your target’s smartphone. Interestingly, it’s often easier to install this app on a spouse’s phone compared to a friend’s. This difference usually comes down to accessibility and trust.
To overcome this challenge, you might need to brush up on some social engineering skills. These skills can help you casually gain access to someone else’s smartphone without arousing suspicion.
Remote installation:
What if you can’t physically access the target’s phone? Don’t worry; remote installation is still on the table. The key lies in convincing or subtly tricking the phone owner into installing the app themselves. This could involve sending them a seemingly harmless link or persuading them to download an app that actually contains the spy software.
Once installed, the app slips into stealth mode, becoming virtually undetectable to the phone’s user. It quietly monitors all activities, from capturing keystrokes to recording email passwords. The user carries on with their daily phone usage, oblivious to the fact that their actions, including sensitive details like email credentials, are being recorded and sent to your dashboard.
Spying on Desktop Computers
When it comes to desktop computers, using spy apps can be a bit tricky, especially if there’s antivirus or anti-malware software in place. These security programs are designed to detect and block spyware, which includes most keyloggers. I’ve put together a list of free keyloggers that can work on Windows machines, albeit with a catch: you might need to temporarily disable your antivirus software for them to operate effectively.
Hardware-based keyloggers to the rescue:
If you’re in a situation where you can physically access the computer you want to monitor – like keeping an eye on the family PC to stay informed about what your spouse or kids are up to – then consider opting for a hardware-based keylogger. This nifty device, resembling a USB drive, can be quickly and discreetly plugged in between the keyboard and the computer. It silently records all data entered, storing it in its flash memory.
Once installed, these keyloggers are incredibly efficient at capturing keystrokes. They store this data in a temporary file within their flash memory. You can later access this information either over WiFi or by directly connecting the keylogger to your own computer.

For more details on selecting the right hardware keylogger, especially if you need PS2 compatibility, be sure to check out resources on the best hardware keyloggers available.
How do You Protect Yourself from Spy Apps?
Here are some straightforward yet effective strategies to keep these sneaky apps at bay:
- Beware of Suspicious Links: Clicking on a link can seem harmless, but it’s one of the easiest ways for spyware to infiltrate your device. These links could appear anywhere – in an email, a text message, or even on social media. They often come disguised as something legitimate or urgent, luring you into clicking them.
- Install Software and Patches with Caution: It’s not uncommon for spy apps to be disguised as software patches or keygens. They might promise to fix your software or offer a free version of a paid program but come with hidden, malicious intent. Always download software and patches from official websites or verified providers. If it’s not coming directly from a legitimate source, it’s not worth the risk.
2. Phishing: Stealing Password by Creating a Fake Login Page
Phishing is a deceptive and often successful attempt by cybercriminals to steal sensitive information like usernames, passwords, and credit card details. It involves mimicking a trustworthy website to trick people into revealing their private data.
Widely recognized as one of the simplest yet most effective social engineering techniques, phishing is a go-to method for many hackers due to its ease and low cost of execution.
Phishing usually occurs through email or instant messaging. The attacker creates a website that looks strikingly similar to a legitimate one, tricking users into entering their personal details. It can fool even the most tech-savvy individuals, including IT professionals. This simplicity in deceiving users is what makes phishing so dangerous.
The only clear identification of a website is its URL!

Imagine this: You receive an email that looks like it’s from Google, asking you to update your password or personal information. Or perhaps it appears to come from your boss or a coworker, inviting you to edit a document on Google Drive or join a Google Hangout call. These emails often contain links to fake login pages designed to capture your credentials.
If you happen to enter your details on one of these fake pages, your login information gets sent directly to the hacker’s server, while you’re redirected to your actual account page, none the wiser.
Two-Factor Authentication: Not Always Foolproof
Think your Gmail account is safe because you’ve enabled two-factor authentication? Think again. Skilled attackers can sometimes bypass these security measures, maintaining access to your accounts. In fact, I recently wrote a post discussing how two-factor authentication codes can be phished.
Detailed Guide: Phishing – How to create a Fake login Page?
Being vigilant and informed about phishing tactics is key to protecting your sensitive information. Always scrutinize emails and messages that ask for personal data, and stay updated on the latest phishing strategies to keep your digital life secure.
3. Guessing or Resetting Email Password
Have you ever considered how someone might crack an email password without any advanced hacking tools? Surprisingly, it often comes down to good old-fashioned guesswork, combined with a bit of social engineering. This method requires not just technical skills but also a knack for understanding people.
Password guessing revolves around getting inside someone’s head to deduce their personal information. It’s about piecing together clues based on what you know about the person. This approach demands sharp social skills and some clever thinking.
Who Could Be the Hacker?
The hacker in these scenarios is often someone close to the victim. It could be a partner, a close friend, or even a family member. These are individuals who know the victim well enough to make educated guesses about their passwords.
In many cases, the hacker might be an online friend or acquaintance. Let’s say you’ve shared personal details with someone online—things like your date of birth, phone number, favorite movies, or music. Seemingly innocent information like this can be a gold mine for a hacker trying to guess your password.
The Process of Password Resetting
Using the information they’ve gathered, the hacker can attempt to guess your email password or the answers to your email account’s security questions. If they succeed, they can reset the password, set a new one, and gain access to your account. The scary part? There’s a surprisingly high chance they might get the security question right, especially if they know you well.
Being aware of how much personal information you share and with whom is crucial in today’s connected world. A little caution can go a long way in protecting your email and other online accounts from such social engineering tactics.
Detailed guide: Bypass Facebook Security Question to Reset Password
4. Man in the middle attack: A Stealthy Email Hacking Strategy
When it comes to email hacking, the ‘Man in the Middle’ (MitM) attack stands out as a sophisticated yet alarmingly effective technique. Unlike direct password guessing or phishing, MitM attacks involve an invisible interception of communication between two parties—typically, the email user and the email server.
How Does a MitM Attack Work?
Imagine you’re sending an email, and unbeknownst to you, there’s a hacker lurking in your digital communication channel. This hacker quietly intercepts the messages you send and receive, without either party realizing there’s someone eavesdropping. It’s like having a stealthy digital spy who can read, modify, and even send emails on your behalf.
One of the most daunting aspects of a MitM attack is its stealth. These attacks are hard to detect because they don’t necessarily leave obvious traces. The hacker positions themselves in the communication flow, making it seem like everything is running as usual.
Common Scenarios for MitM Attacks
- Unsecured Wi-Fi Networks: Public Wi-Fi hotspots are common grounds for MitM attacks. Hackers can exploit these networks to intercept communications between connected devices and the internet.
- Email Interception: By intercepting the data transmitted during an email exchange, hackers can gain access to sensitive information, manipulate message content, or even impersonate the sender or recipient.
Protecting Yourself from MitM Attacks
- Use Secure Connections: Always ensure you’re using secure, encrypted connections, especially when accessing your email. Look for HTTPS in your browser’s address bar as a sign of a secure connection.
- Be Cautious on Public WiFi: Avoid accessing sensitive accounts like email when connected to public WiFi. If necessary, use a VPN to encrypt your internet traffic.
- Regular Security Updates: Keep your software and security protocols up-to-date. This includes your operating system, email applications, and any security software.
By understanding the mechanics of a man-in-the Middle attack, being aware of the risks and taking proactive steps to secure your communications, you can significantly reduce the likelihood of falling victim to this sophisticated form of email hacking.
How to Protect Yourself from Email Hacking
Protecting your email account from hackers is more crucial than ever. Here are some practical tips to ensure the safety of your email account against potential hacks:
1. Create Strong Passwords
Creating a strong password is your first line of defense. Mix it up with numbers, letters, and symbols to make it more complex. This approach not only wards off brute force attacks but also makes it harder for someone to guess or ‘shoulder sniff’ your password. Consider using a passphrase—a longer, more complex, and more secure alternative to traditional passwords.
2. Avoid Copy-Pasting Passwords
It might seem convenient, but avoid copy-pasting your passwords into login fields. Your browser and other apps can access clipboard data, which could lead to your password being compromised.
3. Keep Your Browser Updated
Regardless of which browser you use, it can be a target for hackers. Regularly updating your browser is essential. Use add-ons or extensions that can detect phishing websites, helping to keep your login credentials safe and your email secure.
4. Be Wary of Phishing Attempts
Phishing emails are a common tool for hackers. Even if an email looks legitimate, be cautious with links. A good practice is to copy the link and open it in your browser’s incognito mode to check its legitimacy.
5. Simplify Online Purchases
Using a single credit card for online transactions makes it easier to track your spending and notice any unusual activity. This can be a simple yet effective way to monitor for potential fraud.
6. Beware of ‘Shoulder Sniffing’
Always be aware of your surroundings when entering your password, especially in public places. Also, avoid the habit of writing down your passwords on sticky notes or other easily accessible places.
7. Scan Downloads for Safety
Before opening software downloaded from unofficial sites, scan it with your antivirus program. To be safer, stick to downloading apps and software directly from the official app stores.
8. Regularly Change Your Passwords
Treat your password like your underwear—change it regularly. This simple habit can significantly improve your account security.
Finally, don’t just focus on specific attack scenarios. Instead, prepare for the highest-risk factors. Think from the perspective of an ordinary person trying to access your data; often, hackers use these simple paths to breach security. Regular vigilance and adopting these practices can significantly enhance your email security.
Related Posts:
- Trace fake Facebook account
- How to hack WiFi password
- Hacking Gmail account password
- Tips to Protect Your Cryptocurrency from Hackers
- Hacking Facebook account
- Best hacking sites & forums
- Is it Safe to Keep your Bitcoins in Crypto Exchange
