Many people are curious about how to protect their Facebook accounts from unauthorized access. This interest has led to numerous questions about how one can hack a Facebook account, reflecting a growing concern over online safety.
Recognizing this concern, our article aims to inform Facebook users about different methods that hackers might use to gain access to accounts.
We will cover seven specific techniques to hack Facebook accounts: phishing, spy apps, DNS spoofing, the “forgot password” method, password guessing, accessing saved Facebook passwords, and man-in-the-middle attacks. Additionally, we’ll also discuss the rise of Facebook hack tools such as Feebhax and why you should avoid them.
This article is written with the intent to educate and inform, providing valuable knowledge on protecting one’s Facebook account against potential security breaches. It’s important for users to understand these methods not to misuse them but to better protect their own accounts from such vulnerabilities.
See also: How to hack email account
7 Ways To Hack Facebook Account

1. Phishing: Creating a Fake Facebook Login Page
Phishing is a common method used to gain unauthorized access to Facebook accounts. This approach doesn’t require advanced technical skills, making it accessible to many. Its effectiveness comes from the creation of fake websites that mimic reputable ones, like Facebook, to trick users into entering their sensitive information, such as passwords.
The process involves setting up a webpage that mirrors the Facebook login page in appearance. However, these fake pages have URLs that, while appearing legitimate at first glance, are actually slightly altered versions of the real Facebook URL. For instance, misleading URLs might be www.facebouk.com or www.faecbook.com.
Victims are lured to these pages and prompted to log in. As they enter their login credentials, the information is sent directly to the person who set up the fake page. In some cases, the data can be captured in real-time as the user types, without even needing them to press the login button.
The success of phishing relies heavily on the user not recognizing the illegitimacy of the page. To protect yourself, it’s important to:
- Verify the URL in your browser’s address bar before logging in.
- Look for security indicators, such as the padlock symbol next to the URL.
- Be wary of links received via email or message that prompt you to log in.
By being aware of these tactics, users can better safeguard their accounts against unauthorized access through phishing attempts.
How to Create a Fake Facebook Login Page?
To create a fake Facebook login page, go to shadowave.com and sign up for your free account. Next, confirm your email and login to your account.
Once logged in, select “Facebook Login Page” from the library of phishing websites, copy the link, and send it to the person you want to steal the login details from. If everything goes well, you will see the password of the victim on the “my victims” page.
The best way to send the phishing link to your victim is by email. Have a look at the screenshot of a phishing email intended to hack a Facebook account.
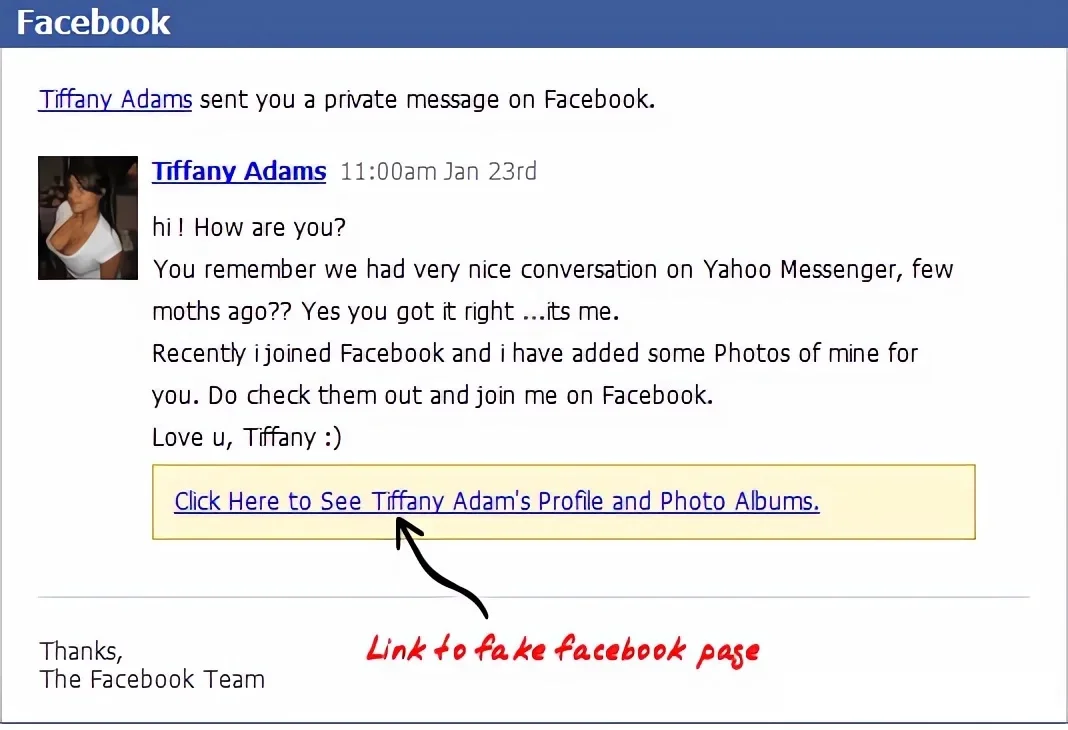
The disadvantage of this method is that it can be challenging to deceive people, as many are already aware of such tactics. However, this method can be ideal for hacking users who frequently browse their Facebook feed on their smartphones. On smaller screens, it’s unlikely that anyone would scrutinize the URL of the webpage.
See also: Facebook Phishing Email Examples
2. Spy Apps: Capturing Facebook Login Credentials
A spy app, often known as a keylogger, is a software tool that records the keystrokes made on a device.
These tools are capable of logging every keystroke, which means they can record information such as usernames and passwords. While keyloggers can serve as monitoring tools, they are frequently used to gain unauthorized access to accounts, making them popular among those looking to hack into Facebook accounts.
Using a keylogger to access someone’s Facebook account is straightforward and practical. Installing and operating such software requires only basic technical skills.
In recent times, mobile spy apps have become more common than their computer counterparts. This shift is largely due to the extensive use of cellphones for social media engagement on platforms like Facebook, Instagram and X (formerly Twitter).
Among various mobile spy applications, mSpy stands out. For someone to use mSpy for Facebook hacking, they must first install it on the intended victim’s smartphone. The app then tracks and logs every keystroke made on the device, including the entry of sensitive information such as passwords.
Get it here: mSpy – ultimate spy app!
mSpy operates in real-time and runs discreetly in the background, making it challenging for users to detect its presence.
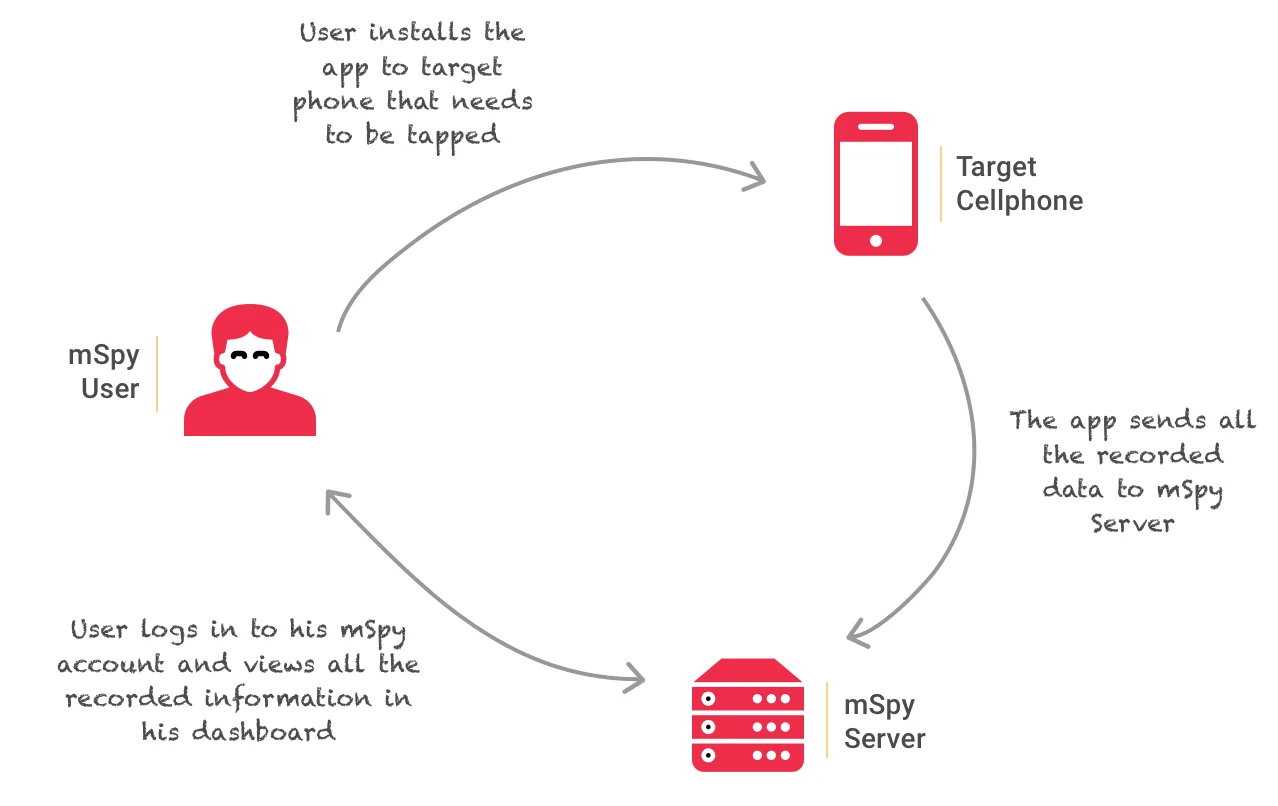
See also: How to tap a cell phone
Apart from keylogging, the mSpy application comes with a range of features designed to track and record various activities on a target smartphone. Here are some of its capabilities:
- Social Media Monitoring: Enables users to view Facebook messages through Messenger, along with activities on WhatsApp.
- Call and Message Tracking: Keeps tabs on call logs and SMS, providing detailed insights into the communications of the device owner.
- Remote Access Tools: Allows for the taking of screenshots, viewing photos and contacts, and other remote monitoring activities.
mSpy has proven useful for those looking to keep an eye on the online activities of their children or spouses. Installing the app on a device you have physical access to, such as your child’s or spouse’s smartphone, is relatively straightforward.
However, deploying the app on a device without direct access presents more of a challenge. Despite this, it’s not out of the range of possibility. Our natural susceptibility to deception means that, with the right approach, installing mSpy remotely can be achieved.
Professional hackers often resort to social engineering tactics to accomplish this. For instance, one might wait for an opportune moment to borrow a friend’s phone under the guise of making a call or browsing the web, using the opportunity to secretly install the app.
See also: 10 free Keyloggers for desktop computers
Hardware Keylogger for Desktop Computers
Keyloggers, tools designed to record keystrokes on a device, come in both software and hardware varieties. Hardware keyloggers resemble USB drives and function by being directly connected to a computer. They must remain attached for as long as needed to complete their task.

These devices have built-in memory and WiFi capabilities, allowing them to store every keystroke, including sensitive information like Facebook usernames and passwords. The stored data can be accessed remotely via WiFi.
To operate, a hardware keylogger is connected between a computer’s keyboard and the computer itself. It silently records all keystrokes into its internal memory. Unlike software keyloggers, hardware versions are compatible with all operating systems, including Windows, macOS, and Linux, because they operate independently of the computer’s software.
Checkout: The Best Hardware Keyloggers
Protecting Yourself from Spy Apps and Keyloggers
To safeguard against these intrusive tools, it’s important to be cautious about your digital interactions:
- Install Wisely: Only download applications and software from reputable sources you trust.
- Be Wary of Unknown Files: Avoid opening documents or files sent from unknown or unverified sources.
- Question Media Sources: Refrain from playing media files obtained from unfamiliar sources.
- Scan External Devices: Always scan USB drives and other external devices with antivirus software before use.
3. DNS Spoofing: Stealing Facebook Login Credentials
DNS spoofing, also known as DNS cache poisoning, is a sophisticated cyberattack technique that poses a significant risk to online security. This type of attack is particularly challenging to detect and can be executed on users who share the same network as the attacker.
The essence of DNS spoofing lies in the attacker’s ability to redirect internet traffic from a DNS server to their own system. Once this redirection is achieved, the attacker can manipulate the traffic to extract sensitive information from the victims, including Facebook login credentials.
For those concerned with cybersecurity, it’s important to understand the basics of how such attacks are structured, not to execute them, but to protect yourself against them. Typically, attackers employ specialized tools and operating systems, such as Kali Linux, which is known for its extensive suite of security and penetration testing tools.
Configuring a system for a DNS spoofing attack involves several technical steps, including modifying system files and setting up network monitoring to intercept and alter web traffic. This process requires in-depth knowledge of network security and should only be understood in the context of protecting one’s own network.
Setting-up DNS Spoofing Attack for Facebook Hacking
This guide is intended for educational use only, to demonstrate the concept of DNS spoofing for hacking Facebook accounts and encourage better protection against such attacks.
Step 1: Prepare Your Environment
- Use Kali Linux OS, a preferred choice for security testing due to its comprehensive suite of tools.
- Confirm that the device used for testing is on the same network (WLAN or LAN) as the test target to simulate real-world conditions accurately.
Step 2: Access Exploitation Tools
- Navigate to the application tab on your Kali Linux interface.
- Select the Social-engineering toolkit (SET) from the Exploitation tools section for further operations.
Step 3: Configuration Adjustments
- Locate and open the ‘etter.conf’ file within the ‘/etc/ettercap/’ directory using a text editor like G-edit.
- Modify the ‘gid’ and ‘uid’ values to ‘0’ for appropriate permissions during the test.
- Adjust settings to enable ‘iptables’ by removing the hash sign (#) next to the relevant line.
Step 4: Launching Ettercap
- Open the Ettercap application through the Terminal with the command
ettercap –G(omit quotes). - Initiate ‘unified sniffing’ via the Sniff menu to begin monitoring network traffic.
Step 5: Network Analysis
- Select the appropriate network interface for sniffing.
- Conduct a host scan to identify devices within the network, then navigate to the ‘Host list’ to choose your test target.
Step 6: Spoofing Demonstration
- Execute a DNS spoofing attack by selecting your target and configuring ARP-poisoning to ‘Sniff remote connections’.
- Use specific commands to direct the target’s traffic through your simulated phishing page, for demonstration purposes.
To safeguard against DNS spoofing attacks on your Facebook account, you should:
- Use secure network connections, ensuring that websites visited have an “HTTPS” prefix in their URL, indicating a secure connection.
- Look for the padlock icon at the beginning of the URL, which signifies that the website’s security certificate is valid.
- Keep antivirus software and network security tools up to date, as they can often detect and prevent unauthorized alterations to network traffic.
Understanding these security measures and implementing them can significantly reduce the risk of falling victim to DNS spoofing and other types of cyberattacks on your Facebook account.
4. Forgot Password Method: Resetting Facebook Password
The “Forgot Password” feature on Facebook offers a method for users to reset their password if they cannot remember it. This approach can also be misused to attempt unauthorized access to someone’s account.
Here’s a step-by-step breakdown of how this method is typically executed:
- Start at Login: Go to Facebook’s login page. Instead of logging in, select the “Forgot Password” option.
- Identify the Account: Enter the email address or phone number of the person whose account you’re trying to access. If the details match an account, Facebook will display the associated profile.
- Account Confirmation: Choose the “This is my account” option when the correct user profile is displayed.
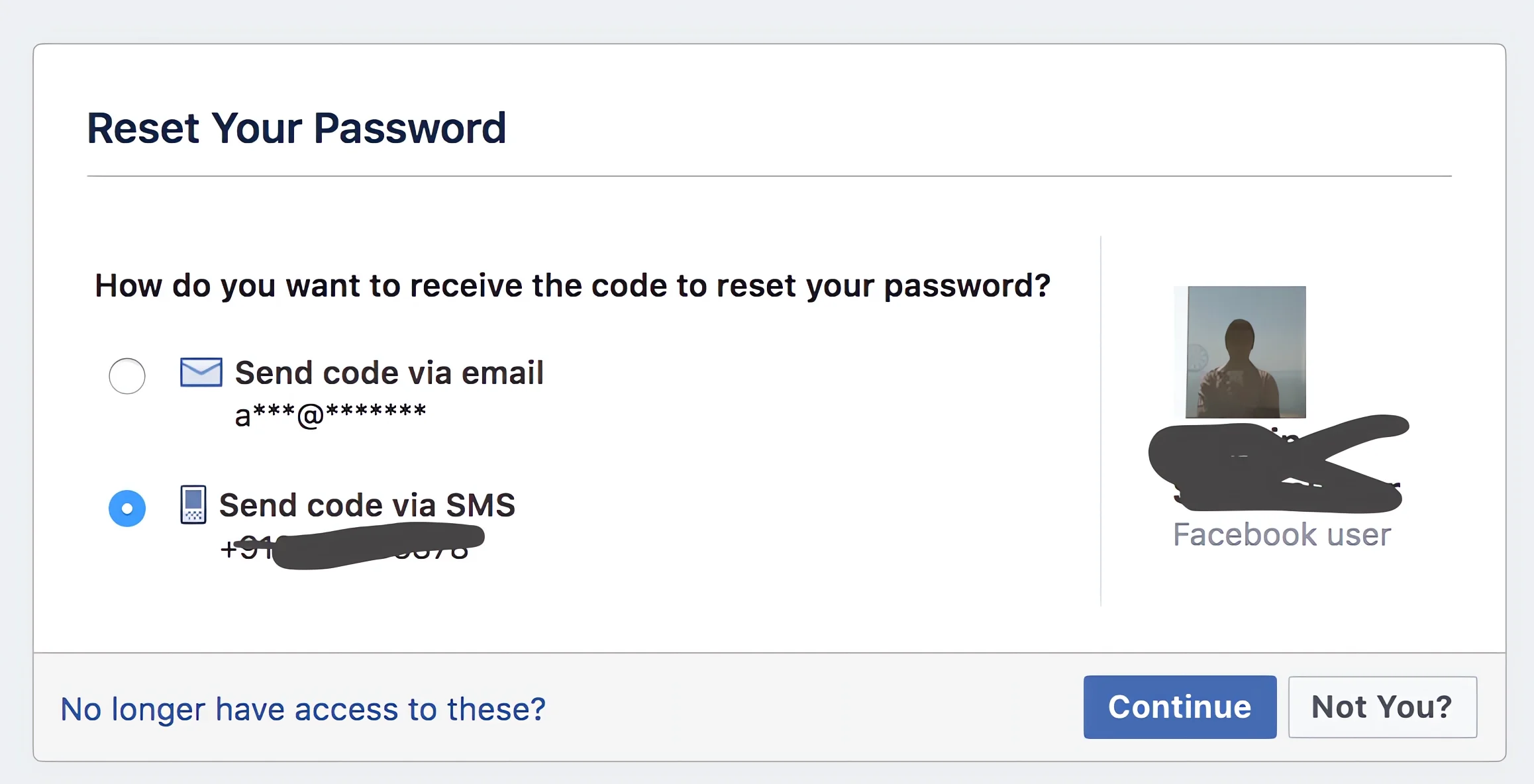
- Recovery Options: Facebook will then ask how you’d like to reset the password, offering linked email addresses or phone numbers as options.
Ways the Password Recovery Process Can Be Exploited:
- Using the Victim’s Cellphone:
If someone has access to the target’s cellphone, they can opt to receive a recovery code via SMS or email. By entering this code, they can reset the password and gain access to the target’s Facebook account. - Answering Security Questions:
If access to recovery methods (phone or email) is unavailable, one can choose the option indicating they no longer have access to these. Facebook will then prompt for answers to security questions. Close acquaintances might guess these answers and proceed to reset the password. - Bypassing Security Questions:
It’s possible to bypass security questions with the assistance of mutual friends. This method involves more detailed steps. To learn more, read how to bypass Facebook security question.
Protecting Your Account:
To defend against unauthorized access through these methods, consider the following steps:
- Regular Monitoring: Keep an eye on your email for any unusual activity alerts from Facebook.
- Strong Security Questions: Choose security questions that are not easily guessable by others, even those who know you well.
- Secure Recovery Options: Ensure your recovery phone number and email are secure and accessible only to you.
- Regular Updates: Keep your contact information and security settings on Facebook up to date.
- Two-Factor Authentication: Activate two-factor authentication for an additional layer of security beyond just the password.
Remember, maintaining the security of your online accounts requires ongoing attention to potential vulnerabilities and taking proactive steps to protect your personal information.
5. Password Guessing: How to Guess Facebook Password
Password guessing is a straightforward approach where someone attempts to hack a Facebook account by guessing the password. This method often works if an individual uses simple or easily guessable passwords.
Common Types of Guessable Passwords:
People might choose passwords that are closely related to their personal life, such as:
- Birthdates, pet names, or the maiden name of a family member.
- Nicknames, the name of a significant other, or the names of close friends or relatives.
- Memorable numbers like old phone numbers, ID numbers, or a cherished car’s license plate.
- Simple sequences or patterns on the keyboard, such as “123456”, “password”, or “QWERTY”.
How Password Guessing Works:
To attempt a password guess:
- Go to the Facebook login page.
- Enter the user’s email or phone number.
- Begin trying different passwords based on potential personal connections or common patterns.
Thinking like the account owner can sometimes help in guessing the password correctly by considering what important names, dates, or numbers they might use.
Protecting Your Account:
To guard against password guessing:
- Create Strong Passwords: Use a mix of letters (both uppercase and lowercase), numbers, and special characters to form complex passwords.
- Avoid Personal Information: Do not include easily obtainable information like birthdates or pet names in your password.
- Enable Login Alerts: In your Facebook security settings, turn on login alerts. This feature sends a notification to your phone or email if a new device or browser logs into your account, allowing you to take immediate action.
- Activate 2FA: Go to your Security Settings on Facebook and look for the option labeled “Two-Factor Authentication”. Follow the prompts to choose your preferred method of 2FA. With 2FA activated, even if someone manages to guess or otherwise obtain your password, they would still need access to the second factor—something only you should have—to successfully log in to your account. This significantly reduces the risk of unauthorized account access.
By following these guidelines, you can enhance the security of your Facebook account and reduce the risk of unauthorized access through password guessing.
6. Accessing Saved Facebook Passwords in Web Browsers
Many individuals choose to save their passwords in web browsers for convenience, which can lead to vulnerabilities, not just with Facebook but also with accounts containing sensitive financial information.
Viewing Saved Passwords:
- Chrome Users: In Chrome, saved passwords can be accessed by typing “chrome://settings/passwords” into the browser’s address bar. If the save password feature is enabled, passwords are hidden by default but can be revealed by clicking an “eye” icon next to the website entries.
- Using WebBrowserPassView: To see saved passwords across various browsers, you can use a tool called WebBrowserPassView. This tool needs to be downloaded and run on the computer in question. The tool can be downloaded without an installer, allowing it to be run from a USB drive. This makes it possible to use the tool on different computers without direct installation.
Protecting Your Accounts:
To safeguard against unauthorized access through saved passwords, consider the following steps:
- Clear Saved Passwords: Regularly delete all saved passwords from your browsers to prevent easy access by others.
- Disable Password Saving: Turn off the browser feature that stores passwords. This setting can usually be found in the privacy or security settings of the browser.
- Manual Login: Without saved passwords, you will need to input your login details each time you access an account, enhancing security.
By taking these measures, you can minimize the risk associated with storing passwords in your browser and ensure your online accounts, especially those containing personal and financial data, remain secure.
You might also like: How to Hack WiFi Password
7. Intercepting Facebook Passwords via Man-in-the-Middle Attacks
A Man-in-the-Middle (MitM) attack occurs primarily on unsecured Local Area Networks (LANs), such as the WiFi found in internet cafés or coffee shops. These locations often attract a large number of users sharing the same internet connection, making them prime targets for attackers.
How It Works:
- Deception: In a MitM attack, the attacker positions themselves between the user’s device and the webserver. Users may believe they are communicating directly with the website, but their data is actually being routed through the attacker.
- Remote Access: The attacker can intercept and access the data transmitted from the victim’s computer without detection, as the connection appears secure to both the server and the user’s device.
- Fake Networks: Attackers may also set up illegitimate WiFi networks to lure unsuspecting victims. Once connected, the victim’s internet traffic, including passwords and sensitive information, is funneled through the attacker’s system.
Tools Used for MitM Attacks:
Attackers employ a variety of tools to execute MitM attacks, including, but not limited to, wireless network adapters, Raspberry Pi computers, and software like WiFi Pumpkin. These tools can intercept and capture data, such as Facebook login credentials and credit card information, from connected devices.
Protecting Yourself:
To safeguard against MitM attacks, follow these precautions:
- Use Secure Networks: Always connect your devices, whether laptops or smartphones, to secure, trusted WiFi networks.
- Verify Network Authenticity: Be cautious of WiFi networks in public places and verify their legitimacy before connecting.
- Consider VPN Use: Using a Virtual Private Network (VPN) can encrypt your internet traffic, making it more difficult for attackers to intercept your data on unsecured networks.
By staying vigilant and employing secure practices when using WiFi networks, you can reduce the risk of falling victim to a MitM attack and protect your personal information from unauthorized access.
The Truth About Facebook Hack Tools
The internet is populated with numerous websites and tools such as Feebhax that claim to offer the ability to hack into Facebook accounts, promising to deliver the password of any account.
It’s important to critically assess these claims and understand the reality behind such tools.
- Scam Nature: Many of these so-called Facebook hack tools are scams. They do not function as advertised and often do not have the capability to breach Facebook’s security measures to access user accounts.
- Security Risks: Engaging with these tools or websites can pose significant security risks. Many are sources of malware, designed to harm your device or steal your personal information rather than help you hack into accounts.
- Unreliable Results: The passwords and login data provided by such applications are almost always incorrect or useless, rendering the use of these tools a waste of time and effort.
- Monetization Tactics: These tools often require users to complete surveys or perform specific actions to access the supposed password file. However, even after completing these tasks, there’s no guarantee of success. The primary goal of these tools is to generate revenue for their creators, not to provide a service.
Why You Should Avoid Facebook Hack Tools:
Given the dubious nature of Facebook hack tools, it’s advisable to steer clear of them for several reasons:
- Privacy and Security: Protecting your digital privacy and security should be a priority. Engaging with these tools can compromise both.
- Wasted Efforts: The time and energy spent attempting to use these tools could be better utilized elsewhere.
- Ethical Considerations: Attempting to access someone else’s account without their permission is unethical and violates Facebook’s terms of service.
Protecting Yourself:
To safeguard against the potential threats posed by these hack tools, consider the following steps:
- Use Strong Passwords: Ensure your Facebook account and other online accounts are secured with strong, unique passwords.
- Enable Two-Factor Authentication: Adding this extra layer of security can significantly reduce the risk of unauthorized access.
- Be Skeptical: Question the legitimacy of any tool or service that claims to offer unauthorized access to accounts.
Understanding the reality of Facebook hack tools is crucial for maintaining online safety and integrity. It’s always better to approach online interactions and claims of account hacking with caution and skepticism.
In wrapping up, it’s vital to understand the implications and ethical considerations of seeking information on hacking a Facebook account. While the curiosity or need to monitor online activities might seem justified in certain contexts, such as institutions overseeing employee productivity or parents keeping tabs on their children’s online safety, the approach to achieving this must be handled with care and responsibility.
Rather than resorting to hacking, which is illegal and unethical, consider legitimate monitoring tools that offer transparency and legality. Tools like mSpy are designed for legal monitoring purposes, allowing parents to supervise their children’s online activities or employers to track company device usage, with the necessary consent from all parties involved.
FAQs
Here are some frequently asked questions related to Facebook hacking:
How to Hack Facebook Password?
To hack a Facebook password, you can use any of the seven hacking methods discussed in this article, namely phishing, spy apps, DNS spoofing, the ‘Forgot Password’ method, password guessing, accessing saved Facebook passwords, and man-in-the-middle attacks.
Why Do People Hack Facebook?
People might hack Facebook accounts for several reasons, including identity theft, financial gain, or spreading malware. It’s important to understand these risks to better protect your account.
How to Report a Facebook Hack?
If your Facebook account has been compromised, report it immediately to Facebook through their Help Center. They offer a step-by-step process to help you regain control of your account.
How to Fix a Facebook Hack?
To recover from a Facebook hack, immediately change your password, review your login activity for anything suspicious, remove any unauthorized apps or sessions, and alert your friends that your account was compromised.
How Do People Hack Your Facebook?
People can hack Facebook accounts through phishing attacks, guessing passwords, or exploiting security vulnerabilities. Knowing these methods can help you guard against them.
How to Hack Facebook Messenger?
You can hack someone’s Facebook Messenger by either using a phishing link or by installing a spy app on their phone. If you opt for phishing, you will need to send them a phishing link and persuade the victim to log in to Messenger using a web browser. Once they log in, you will obtain their login credentials. On the other hand, if you install a spy app on their phone, you will be able to read all their Messenger chats.
Why Do Hackers Hack Facebook?
Hackers may target Facebook accounts to gather personal information, spread spam or malicious software, or for financial gain through scams. Awareness can help you take preventive measures.
How Can I Hack Back Into My Facebook Account?
If your Facebook account has been hacked, use the “Forgot Password” option on the login page and follow the instructions provided by Facebook to regain access.
What to Do If Someone Is Trying to Hack Your Facebook?
If you suspect an attempt to hack your Facebook account, change your password immediately, enable two-factor authentication, and alert Facebook through their reporting tools.
How to Prevent Facebook Hacking?
To prevent your Facebook account from being hacked, regularly update your password, enable two-factor authentication, be cautious of phishing scams, and limit the personal information you share online.
How to Create Your Own Facebook Hacking Software?
To create your own Facebook hacking software, you need knowledge of coding, depending on which platform you aim to target. For example, if you want to target Android users, knowledge of Android development is required.
How to Hack Facebook Accounts for Free Without Downloading Anything?
To hack Facebook accounts for free without downloading anything, you can use the phishing technique or the ‘Forgot Password’ method discussed in this article.
How to Download Facebook Hacking Software?
You cannot download Facebook hacking software because it does not exist. If you find it anywhere or if anyone is selling it, please rest assured it’s a scam.
How to Hack Someone’s Facebook Without Email?
To hack someone’s Facebook without email, you could send a phishing website link via Messenger or, if you have access to their device, install a spy app.
How to Hack Facebook using Termux?
Termux is a terminal emulator for Android that enables the operation of a Linux environment directly on an Android device. To hack Facebook using Termux, you will need to use hack tools developed for Kali Linux on Android.
Related Posts:
- How to Find Someone’s IP Address
- Gmail Hacker: Hack Gmail password
- Finding Someone’s Location on Facebook
- How to Find out who made a Fake Facebook Account
- Get Somebody’s IP Address on Messenger
- Funny Facebook Hacking Statuses
- Best Hacking Sites & Forums for Hackers
