With cyber threats evolving every day, it’s crucial to bake security right into the software development life cycle (SDLC). This isn’t just about fixing issues as they pop up; it’s about preventing them from happening in the first place.
And the best part? A secure SDLC not only protects against cyber threats but also saves time and resources in the long run, ensuring your software is trustworthy and resilient.
There are various ready-made frameworks available for securing the Software Development Life Cycle, and many companies offer services to implement these effectively. For instance, Litslink, a leader in software development, takes security seriously. They have established a comprehensive security framework that is integral to every stage of their SDLC. This approach is not merely an added feature; it is central to their entire process.
In this article, we have listed some of the best practices for securing SDLC and strategies for integrating security into SDLC.
Best Practices for Securing the SDLC
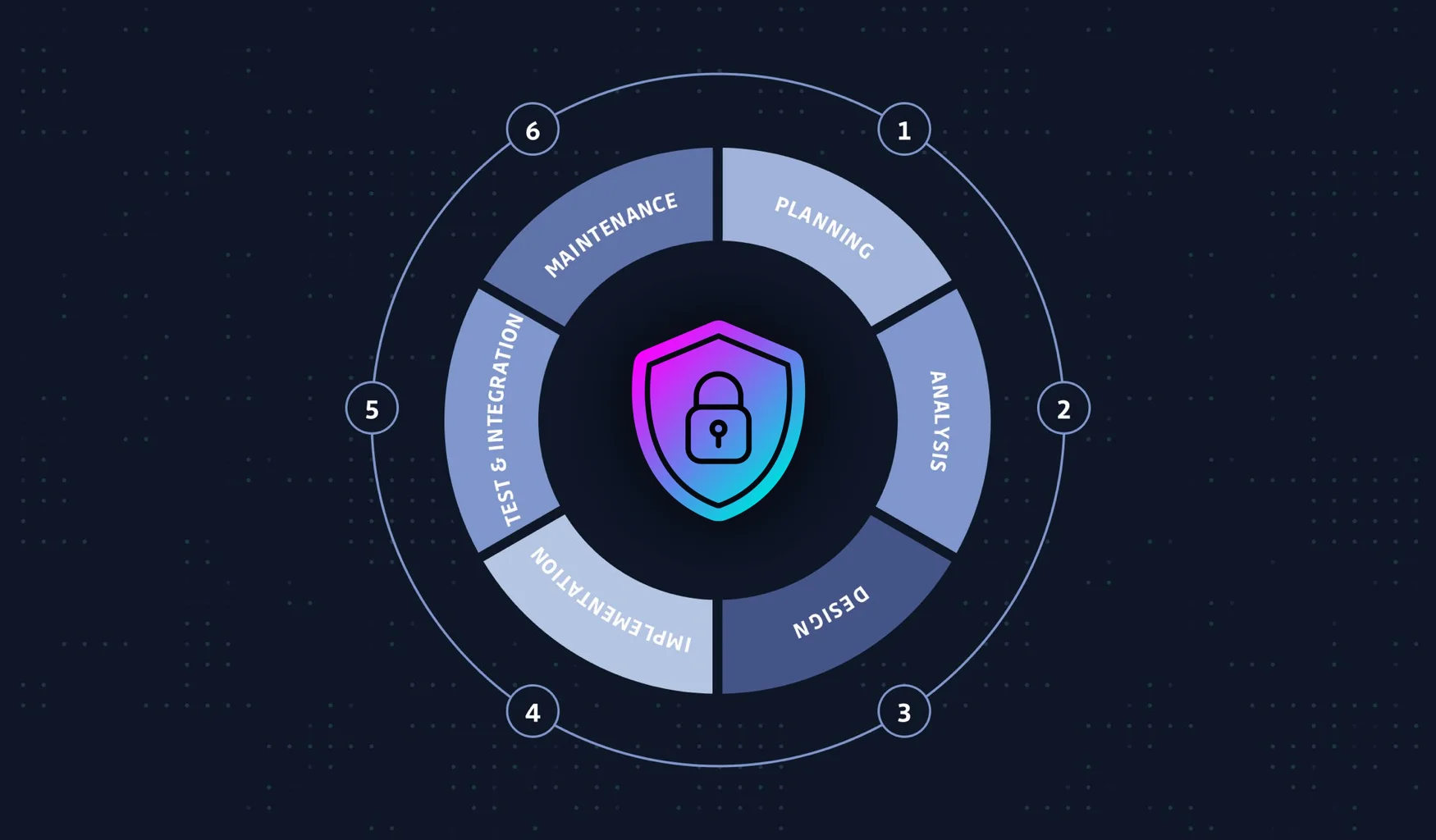
Securing the SDLC requires a holistic approach that integrates security practices into every stage of the development process. This shift towards “shift-left security” helps identify and address security issues early on, before they can cause significant damage.
Here are some best practices you can follow to secure your SDLC:
- Threat Modeling: Conducting threat modeling early in the SDLC helps identify potential vulnerabilities and design appropriate security controls to mitigate risks.
- Static Application Security Testing (SAST): SAST tools analyze the source code of applications to identify potential vulnerabilities before they are compiled into executables.
- Dynamic Application Security Testing (DAST): DAST tools simulate attacks on running applications to identify vulnerabilities in the application’s runtime behavior.
- Input Validation and Sanitization: Thoroughly validating and sanitizing user input can prevent malicious code from being injected into applications, leading to security breaches.
- Secure Coding Practices: Emphasize secure coding practices among developers, including avoiding common coding mistakes that can introduce security vulnerabilities.
- Dependency Management: Carefully manage dependencies to ensure that only secure and up-to-date libraries and frameworks are used in applications.
- Vulnerability Management: Continuously monitor for and remediate vulnerabilities in the software supply chain and applications.
- Penetration Testing: Regularly conduct penetration tests to simulate real-world attacks and identify and address potential security weaknesses.
Strategies for Integrating Security into the SDLC
- Establish a Security Culture: Foster a security-conscious culture within the organization, emphasizing the importance of security throughout the SDLC.
- Automate Security Tests: Integrate security testing tools and processes into the automated build and deployment pipeline to streamline security checks and reduce manual effort.
- Adopt DevSecOps: Implement DevSecOps practices to break down silos between development and security teams, promoting collaboration and shared responsibility for security.
- Use Security Tools and Frameworks: Leverage security tools and frameworks specifically designed for SDLC security, such as open-source tools like SonarQube and OWASP ZAP.
- Educate and Train Developers: Provide regular security training for developers to enhance their understanding of secure coding practices and security best practices.
- Involve Security in Design and Architecture: Include security experts in the early stages of design and architecture discussions to ensure security is considered from the outset.
- Document Security Requirements: Clearly document security requirements and expectations for each stage of the SDLC to ensure alignment and consistency.
- Establish a Security Testing Policy: Define a comprehensive security testing policy that outlines the types of tests to be performed, the frequency of testing, and the ownership of security testing activities.
- Continuously Monitor and Improve: Continuously monitor and evaluate the effectiveness of security practices and make adjustments as needed to adapt to emerging threats and evolving technologies.
So, wrapping it up, think of security in the SDLC as the secret sauce to safer software. When you start focusing on security right from the get-go, you’re setting up your software to be tough against threats. It’s like giving your software a shield against those sneaky security bugs and breaches. But hey, this isn’t just ticking boxes for compliance. It’s about earning the trust of your customers and stakeholders. You’re not just protecting your code; you’re safeguarding your business’s heartbeat and the confidence of your users.
Now, how do you make this happen? It’s a mix of sticking to best practices, rolling out smart strategies, and, most importantly, nurturing a culture where everyone’s thinking security-first. That’s how you tighten up your software’s defense and pave the way for a future where your apps and your users are in a safer, more secure digital world.
Related Articles:
- Startup Software Development Process: Crucial Factors to Consider
- Top 11 Enterprise Software Development Trends to Watch in 2024
- Tailored Software Development: A Catalyst for Your Business Growth
- Scaling Software Development Teams: Challenges And Solutions
- Maintaining Software Quality at Speed – Agile Testing Strategies
- How to Design a Secure File Upload Process for Your Users
- The Essential Cybersecurity Checklist for Your Fintech Application
- NIST Penetration Testing Framework: A Comprehensive Guide
