Recently an anonymous trader has gained attention in the decentralized finance (DeFi) world after accumulating large profits and fees using a strategy called sandwich attacks. It has been observed that the bot belonging to the anonymous trader made about $1.67 million in two days, bringing the total profits for sandwich attack traders to almost $4 million in one month.
Every month, crypto traders suffer millions in losses due to sandwich attacks on their transactions. Numerous sandwich attack bots persistently monitor the mempool, searching for transactions they can front-run.
It has been challenging for traders to determine the susceptibility of their swaps on decentralized exchanges to sandwich attacks.
Mempool: short for memory pool, is a temporary storage area for unconfirmed transactions in a cryptocurrency network. When a transaction is initiated, it first enters the mempool before being verified and included in a block by miners.
Front-run: front-running refers to the unethical practice of a trader executing orders on a security based on advance knowledge of pending orders from other clients or market participants.
What are Sandwich Attacks?
Sandwich attacks, also known as ‘front-running’ attacks, are a type of exploit (using sandwich attack bots) that occurs on decentralized cryptocurrency exchanges and trading platforms, primarily those based on Ethereum.
These attacks take advantage of the transparency of blockchain transactions and the nature of how transactions are processed.

In a sandwich attack, the attacker monitors pending transactions on the blockchain and identifies a target transaction, such as a large trade order.
The attacker then places their own buy order with a higher gas fee than the target transaction, effectively ‘front-running’ it and ensuring that their transaction gets processed before the target one. Once the attacker’s buy order is executed, they immediately place a sell order after the target transaction, again with a higher gas fee to ensure quick processing.
The sandwich attack can cause the price of the targeted token to temporarily increase due to the attacker’s buy order, which in turn leads to the target transaction executing at a higher price.
The attacker then profits by selling the tokens at this higher price immediately after the target transaction has been executed. The victim, in this case, may end up paying a higher price for the token than they initially intended, while the attacker capitalizes on the temporary price increase.
If you want to stay away from such fraudulent activities and avoid becoming a victim, it’s essential to use a reputable sites such as bitcoin circuit.
Types of Sandwich Attacks
There are two distinct types of sandwich attacks, which have similar strategies but involve different actors.
In the first attack, the adversary acts as a liquidity taker, while in the second, they act as a liquidity provider. Regardless of the attacker’s role, the sandwich attack follows these steps:
Step 1: Identify a victim’s transaction that exchanges asset X for asset Y.
Step 2: Frontrun the victim by performing a similar action, such as exchanging asset X for asset Y.
Step 3: Allow the victim to execute their transaction. Due to the frontrunning in step 2, the victim experiences higher slippage, meaning they trade at a significantly worse price than anticipated.
Step 4: Backrun the victim with another action, like exchanging asset Y back to asset X. Steps 2 and 4 together should create a risk-free arbitrage opportunity for the attacker.
Here’s an example:
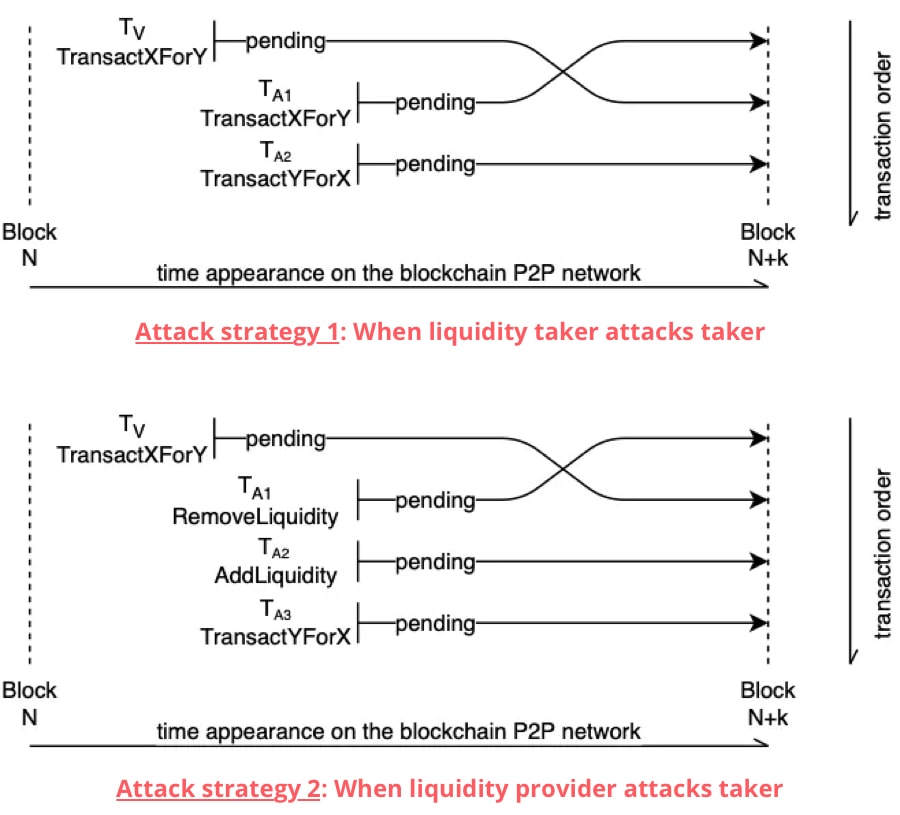
A victim transaction involves trading one cryptocurrency asset X (e.g., ETH, DAI, SAI, VERI) for another asset Y, making a large purchase. A bot detects this transaction and frontruns the victim by buying asset Y before the large trade is executed. This purchase raises the price of asset Y for the victim, increasing the slippage (the expected price increase or decrease based on the trading volume and available liquidity).
As a result of the bot’s large purchase of asset Y, its price goes up, causing the victim to buy asset Y at a higher price. The attacker then takes advantage of the increased price by selling asset Y, making a profit.
Sandwich Attack Bot Download
Typically, cryptocurrency bots designed for sandwich attacks and similar strategies are not available for free, as they often cost thousands of dollars. However, a GitHub user named lightning0125 has made a free sandwich attack bot available for use.
This bot has limited features compared to the full-featured, paid version of a sandwich attack bot. It is a multi-chain DeFi trading bot that includes sandwich trading capabilities, a front-run bot, and a demo account function.
While this free alternative may be appealing to some users, it’s essential to be cautious when using such tools and consider potential security risks and ethical concerns related to exploiting vulnerabilities in decentralized exchanges.
You can download the bot from here: Sandwich Trading Bot
The cost of full-featured sandwich attack trading suite is $1200. This particular lite version of the full-featured bot only produces 3 transaction per hour. If you are interested in purchasing the original bot, you can send an email to the author at ps-lightning.workplace@gmail.com.
How to Maximize Your Profit Using Sandwich Attack?
The profit from a sandwich attack is the difference between the tokens received in the final sale and the tokens spent in the initial purchase. The initial reserves and the victim’s trade amount are fixed; the only variable under the attacker’s control is the initial trade amount in the frontrun.
With flash loans, an attacker can essentially acquire an unlimited number of tokens, eliminating the need to set a limit on the attacker’s available funds. It might seem that trading as many tokens as possible would yield the most profit.
However, this would only be true if there were no fees involved. In reality, the sandwich attacker must pay a 0.3% fee twice, and the higher the input amount, the higher the fees paid.
It’s essential to note that the profit has an upper limit, which is the victim’s trade amount. The attacker cannot receive more tokens in the final trade than what was input in the first two trades. As a result, when the fees exceed the victim’s trade amount, the attacker no longer makes a profit.
In conclusion, the sandwich attacks are a concern in the decentralized finance (DeFi) space, as they exploit the openness and transparency of blockchain technology.
Various solutions have been proposed to mitigate the risk of sandwich attacks, including the implementation of more sophisticated trading algorithms, the use of privacy-enhancing technologies, and the adoption of new consensus mechanisms that make it more difficult for attackers to manipulate transaction ordering.
Related Posts:
- Is it Safe to Keep your Bitcoins in Crypto Exchanges
- Tips to Protect Your Cryptocurrency from Hackers
- Crypto Payment Gateway without KYC – 4 Options
- Real BitCoin Generator Hack tool – Does it work?
