Disclaimer! : This article is for information purpose only. We do not encourage you in any manner to try these Methods on anyone.
In my last post about Facebook hacking, I had mentioned something called web cookie stealing and I had also promised to post more information about the same. In this post I have discussed about how you can steal session cookies over WiFi Network or when in a LAN connection using a technique called Sidejacking (Facebook sniffer).
When you log in to any website by submitting your username and password, First the server checks if an account matching this information exists and if so, replies back to you with an “authentication cookie” which is then stored by your browser for all subsequent requests and to keep you logged in.
What is Sidejacking?
Sidejacking attack (also called as session hijacking) is when an attacker gets a hold of a user’s cookie, allowing them to do anything the user can do on a particular website. In other words, the attacker can now make use of your cookie to impersonate your account and can do everything a user can do when logged-in to any website.
It’s very common, that many Websites protect your account by encrypting the login process. But it is very uncommon for Websites to encrypt everything else after you login(eg: cookies).

This makes the cookie and the user vulnerable. On an open wireless network like WiFi, cookies are basically shouted through the air, making these type of attacks extremely easy, yet very popular websites continue to fail at protecting their users.
The Sidejacking attack involves two major steps
Capturing packets (session cookie)
There are a wide variety of tools available that can Sniff packets containing “session cookies“. Use any packet sniffer such as Wireshark to sniff the packets between the target IP and the host. These tools can capture packets such as POST or GET requests used by Web-browsers to send and receive data from the HOST.
But we are mainly interested in grabbing the cookies, so carefully takeout the cookie information from the sniffed Packets. Popular packet Sniffers: WireShark, Ethereal, etc.
Using captured session cookie
Once you have the cookie information, the next task is to use this information to get access to the victim’s user account. Using Sniffed Cookie you can actually login to your victims account even without knowing his/her password.
To do this you will require browser plugin that can manage and edit cookies. For Firefox Browser, you can use Cookie Manager+ or Edit Cookies to do this task. Chrome users can check out: Edit This Cookie or Cookie Manager.
Easiest method to hijack session (SideJacking)
The above method is cumbersome of course and requires more time. To simplify this Task, Mr.Eric Butler a software engineer introduced a Firefox extension called Firesheep.
The extension was created as a demonstration of the security risk to users of web sites that only encrypt the login process and not the cookie(s) created during the login process.
The extension uses a packet sniffer to intercept unencrypted cookies from certain websites, as the cookies are transmitted over the networks.
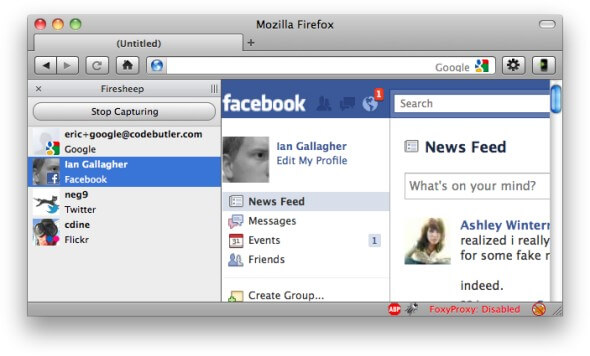
When you are on public WiFi or LAN, Fireship can automatically capture all the available session cookies of any website and reports it to you. You can now choose between all the available user accounts and you are just a click away to access them.
As you can see above, It shows the discovered identities on a sidebar displayed in the browser and allows the user to instantly take on the log-in credentials of the user by double-clicking on the victim’s name.
Download: firesheep-0.1-1 for Windows & OS XFiresheep has exploited and made it easy for public wifi users to be attacked by session hijackers. Websites like Facebook, Twitter, and any that the user adds to their preferences allow the Firesheep user to easily access private information from cookies.
How do I protect myself from SideJacking attack?
- It is very easy to protect yourself against this sort of attack. Both Facebook & Twitter support HTTPS, so when you browse Facebook (or Twitter for that matter) On Public Wifi or LAN, please make sure you’re using HTTPS rather than HTTP in the URL.
Facebook: Account Settings >> Account Security >> check “Secure Browsing (https)” >> Save.
Twitter: Settings >> Account >> check “Https Only” >> save. - FireFox Users can use Plugin called HTTPS Finder. HTTPS Finder automatically detects and alerts when SSL is available on a web page. It also provides one-click rule creation for HTTPS Everywhere.
- When you are using Public WiFi, Avoid Logging-in on Websites that don’t Support HTTPS. Don’t use sites that revert back to HTTP after login.
- Always Log off websites when done. If the ‘victim’ logs out of any Website, the attacker’s session becomes invalid – so it’s a good practice to actually log out and log back in again rather than using the ‘remember me’ check-box.
- Avoid using unencrypted WiFi. Encrypting everything over WiFi is an excellent idea. Although not many hot-spots offer Encrypted WiFi, using it can greatly reduce the risk of being hacked.
Relates posts:
- Best hacking websites list
- How to hack email
- Tracking Facebook user location
- How to hack WiFi password
- Finding someones IP on Facebook
