Disclaimer! : This article is for information purpose only. We do not encourage you in any manner to try any kind of hacking methods discussed in this article.
Security researchers have found that, any android smartphone running on android version 2.2 to 5.1 (includes Lollipop and KitKat) can be hacked using this new vulnerability found in the heart of Android. According to the statistics, more than 950 million android smartphones and tablets are vulnerable to this attack.
The vulnerability lies in the component called “Stagefright” that resides right in the heart of android operating system. Its a core component the Android OS, which is responsible for processing multimedia files (videos, audio files and documents).
In short, whenever you play any video or audio on your android smartphone, this core component runs in the background which processes every bit of information to present the multimedia file on the screen.
This “stagefright” component is implemented in native code (C++) instead of memory-safe languages like Java, since media processing is time-sensitive. This itself can lead to memory corruption.
Researchers therefor examined deepest corners of this scary looking “stagefright” code and found multiple “remote code execution vulnerabilities” that can be exploited using various hacking methods, the worst of which requires only mobile number of victims. We will see how the methods to hack android smartphone remotely works in the below section.
“Remote code execution is the ability of an attacker to access someone else’s system and make changes, no matter where the system is geographically located.”
One of the researchers quoted that, “Unlike spear-phishing, where the victim needs to open a PDF file or a link sent by the attacker, this vulnerability can be triggered while you sleep. Before you wake up, the attacker will remove any signs of the device being compromised, and you will continue your day as usual—with a trojaned phone.”
This vulnerability carry more serious security implications. Exploiting this vulnerability, hackers can hack millions of android smartphones and steal their data. After hacking mass number of android devices, hackers can even make a botnet network of hacked device.
Methods to trigger Stagefright vulnerability:
Sending exploit via MMS message
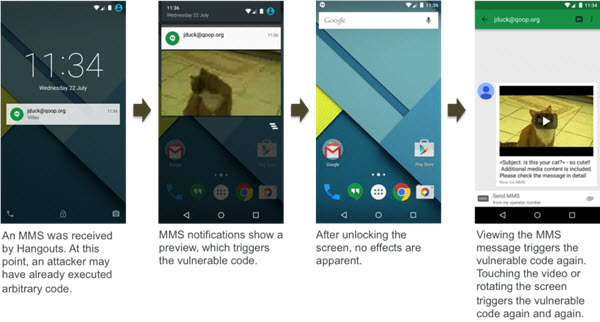
Here the hacker only needs your mobile number, using which he will first send you a specially crafted MMS (multimedia message) containing possibly an .MP4 file. And when the MMS containing the .MP4 file gets downloaded, The hacker will then be able to remotely execute malicious code on your smartphone that can lead to data loss or compromise your sensitive data, depending on the purpose.
The very fact that you get a preview of any message received over the air on all the latest versions of Android, this means that the attached media file (.MP4 file) also gets downloaded automatically. This makes this vulnerability very dangerous as it doesn’t require you to take any action to be exploited.
The hacker can just send the MMS, trigger the code, and wipe the MMS signs (even delete the message before you see it) while you sleep at night. Next morning you will continue using your affected smartphone without knowing that it is compromised.
Here is the actual workflow of this exploit method:
Embed exploit in Android application
In the previous hacking method, the hacker had to know the mobile phone number for triggering exploit via MMS. With that approach if the hacker wanted to compromise large number of smartphone, he should be able to gather large number of mobile numbers first and then invest money in sending out MMS messages to these victims.
In this method the hacker need not know phone numbers to carry out mass hacking. He could just embed the exploit in apps and play the infected mp4 file to trigger the exploit. watch the proof of concept below:
HTML exploit to target website visitors
The hacker simply embeds the same malformed MP4 file into a HTML web page and publishes the page online. When the visitor comes in, he is presented with a video that auto plays triggering the exploit taking advantage of “Stagefright” vulnerability. This kind of attack method is very dangerous since you can lure victims to websites easily than asking them to install apps. Watch the proof of concept below:
The security researcher who discovered this vulnerability will be presenting his full findings, including six additional attack methods to exploit the vulnerability, at Black Hat security conference in Las Vegas on on august 5 and DEF CON 23 on August 7, where he is scheduled to deliver a talk.
Also the researcher had even informed google about the exploit with possible patch within few hours of discovery. Google acted immediately and patched its latest version.
Am i safe from this “Stagefright” exploit?
As i said google has already received patch and has fixed its latest version of android, Only few high end smartphones running latest version will get the patch immediately. Others will have to wait for some time due to slow update cycle.
The various device manufacturers are yet to acknowledge the fix given by google and it will take some time for scheduling over-the-air updates from companies such as Samsung or Motorola. Again this fix will not help Millions of Android users that owned older versions of the operating system that Google no longer supports. So you better take preventive measures.
How to avoid being victim of “Stagefright” attack?
Since large number of android users running older version of android will not be able to get patch and it is up to each device manufacturer to patch the devices against Stagefright attack, Its always good to become aware of the risks and take preventive measure.
- You can protect yourself from MMS attack by turning off MMS auto-retrieval int he messaging settings.
- Never open MMS message from Unknown Numbers, delete them immediately.
- Always install apps from Official google playstore and always read reviews before installing any.
- Do not click or visit any suspicious links with catchy or luring titles.
Make sure you follow above preventive measure and also inform your friends and family. If you have any doubts regarding this exploit then please feel free to comment below.
Source: Zimperium blog
